Published on , commented on March 10, 2023
Anyone Can Get IPv6 PI Space – Buy More RAM and TCAM?
Till a few weeks ago, you could get provider-independent (PI) IPv6 address space in RIPE region only if you “demonstrated that you’ll be multihomed”, which usually required having nothing more than an AS number. With the recent policy change, anyone can get PI address space (and this is why you should get it) as long as they have a sponsoring LIR, and the yearly fee for an independent resource (RIPE-to-LIR) is €50.
See you @ PLNOG in Warsaw
The 8th PLNOG meeting starts in less than a week and the fantastic Andrzej Targosz has yet again kindly invited me to talk about cloud networking and data center fabrics (the first session is on Monday afternoon, the second one on Tuesday morning). I’ll be in Warsaw from Sunday evening to late Wednesday morning, so if you’d like to meet me, ask me a really tough question (layer-2 DCI is off-limits), discuss your network design, or just drink a cup of coffee or a beer with me (please don’t mention vodka), send me an e-mail and we’ll figure out where and when to meet.
Does CCIE still make sense?
A reader of my blog sent me this question:
I am a Telecommunication Engineer currently preparing for the CCIE exam. Do you think that in a near future it will be worth to be a CCIE, due to the recent developments like Nicira? What will be the future of Cisco IOS, and protocols like OSPF or BGP? I am totally disoriented about my career.
Well, although I wholeheartedly agree with recent post from Derick Winkworth, the sky is not falling (yet):
Edge Virtual Bridging (802.1Qbg) – a Technology Refusing to Die
I thought Edge Virtual Bridging (EVB) would be the technology transforming the kludgy vendor-specific VM-aware networking solutions into a properly designed architecture, but the launch of L2-over-IP solutions for VMware and Xen hypervisors is making EVB obsolete before it ever made it through the IEEE doors.
Embrace the Change ... Resistance Is Futile ;)
After all the laws-of-physics-are-changing hype it must have been anticlimactic for a lot of people to realize what Nicira is doing (although I’ve been telling you that for months). Not surprisingly, there were the usual complaints and twitterbursts:
Updated Webinar Roadmaps
I finally found just the right set of tools to draw and update webinar roadmaps without too much hassle, and updated all of them to include the webinars developed during late 2011 and planned for 2012:
NEC+IBM: Enterprise OpenFlow you can actually touch
I didn’t expect we’d see multi-vendor OpenFlow deployment any time soon. NEC and IBM decided to change that and Tervela, a company specialized in building messaging-based data fabrics, decided to verify their interoperability claims. Janice Roberts who works with NEC Corporation of America helped me get in touch with them and I was pleasantly surprised by their optimistic view of OpenFlow deployment in typical enterprise networks.
6WIND: Solving the Virtual Appliance Performance Issues
We all know that the performance of virtual networking appliances (firewalls, load balancers, routers ... running inside virtual machines) really sucks, right? Some vendors managed to offload the packet-intensive processing into the hypervisor kernel, getting way more bang for the buck, but that’s a pretty R&D-intensive undertaking.
We also know that The Real Men use The Real Hardware (ASICs and FPGAs) to get The Real Performance, right? Wrong!
IBM launched a Nexus 1000V competitor
Three days ago IBM launched Distributed Virtual Switch 5000V, its own distributed vSwitch for VMware ESX platform. On one hand, it proves Cisco has been going the right way with Nexus 1000v (just in case you wondered), on the other hand, things just got way more interesting – IBM is obviously returning to networking.
Visiting the Ivory Tower
Just before 2011 hit its expiration date, Derick Winkworth published Being Good at IT Stuff where among a gazillion things I totally agree with he also wrote “Even in IT, an IT degree is useless.”
I know exactly why he wrote that; I’d attended plenty of seemingly useless lectures (although it turns out sometimes it pays to understand those topics), and some people still think teaching History of Computer Engineering or obscure programming languages makes perfect sense.
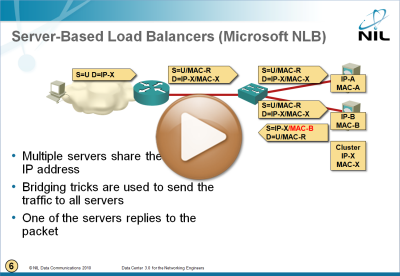
Microsoft Network Load Balancing Behind the Scenes
I figured out I wrote a lot about Microsoft Network Load Balancing (NLB) without ever explaining how that marvel of engineering works. To fix that omission, here’s a short video taken from the Data Center 3.0 webinar.
Bandwidth-On-Demand: Is OpenFlow the Silver Bullet?
Whenever the networking industry invents a new (somewhat radical) technology, bandwidth-on-demand seems to be one of the much-touted use cases. OpenFlow/SDN is no different – Juniper used its OpenFlow implementation (Open vSwitch sitting on top of Junos SDK) to demonstrate Bandwidth Calendaring (see Dave Ward’s presentation @ OpenFlow Symposium for more details), and Dmitri Kalintsev recently blogged “How about an ability for things like Open vSwitch ... to actually signal the transport network its connectivity requirements ... say desired bandwidth” I have only one problem with these ideas: I’ve seen them before.
Buying yearly subscription a bit at a time
One of my readers sent me the following question:
I know that if I purchase a single webinar, I can apply that cost toward a yearly subscription. Is it additive? If I start buying recordings one-by-one until I reach $200, will I be given the yearly subscription?
The answer is a qualified yes (and you can find all the details on my web site):
Nicira, BigSwitch, NEC, OpenFlow and SDN
Numerous articles published in the last few days describing how Nicira clashes heads-on with Cisco and Juniper just proved that you should never let facts interfere with a good story (let alone eye-catching headline). Just in case you got swayed away by those catchy stories, here’s the real McCoy (as I see it):
Nicira Open vSwitch Inside vSphere/ESX
I got intrigued when reading Nicira’s white paper claiming their Open vSwitch can run within vSphere/ESX hypervisor. There are three APIs that you could use to get that job done: dvFilter API (intercepting VM NIC like vCDNI does), the undocumented virtual switch API used by Cisco’s Nexus 1000v, or the device driver interface (intercepting uplink traffic). Turns out Nicira decided to use a fourth approach using nothing but publicly available APIs.