Blog Posts in March 2024
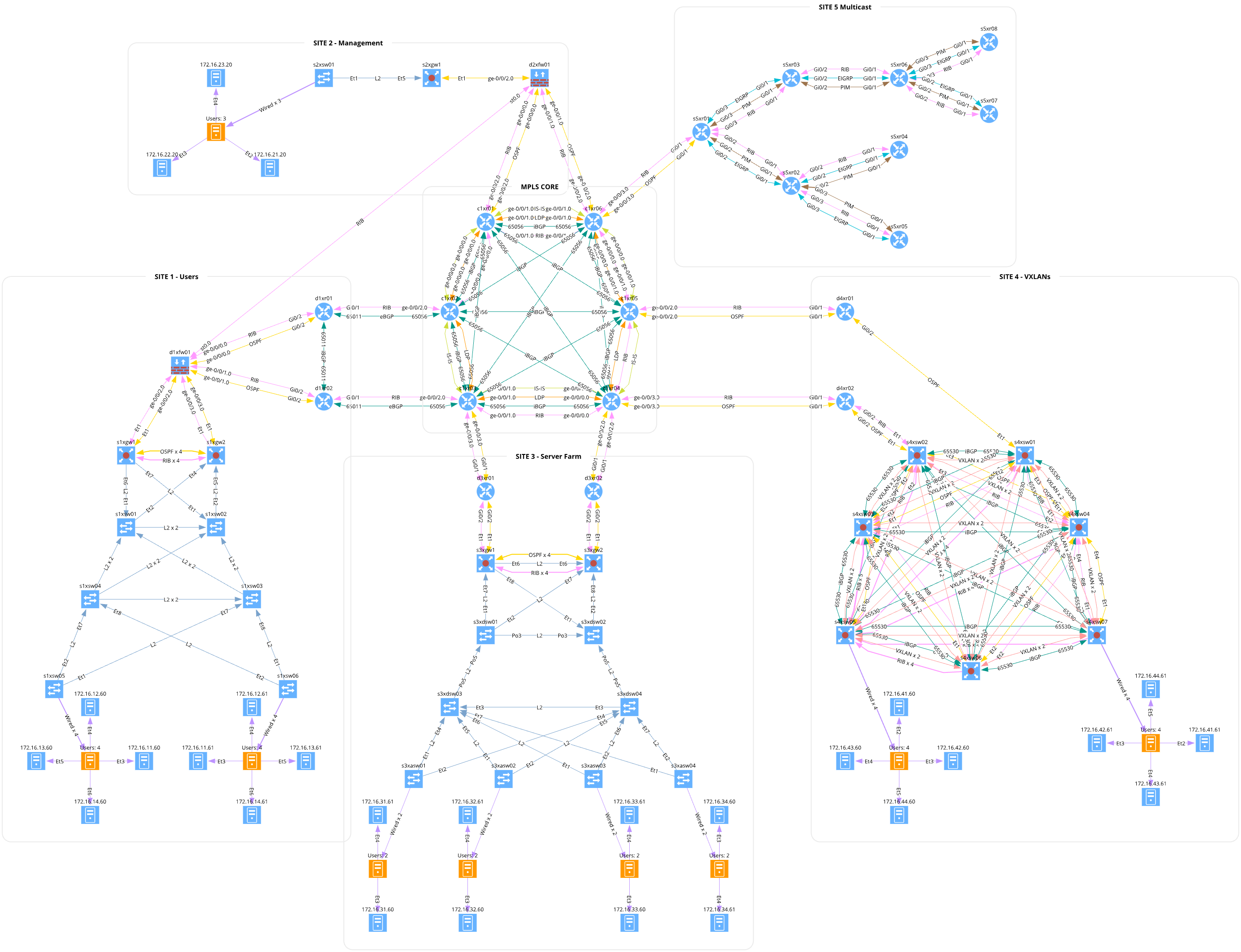
BGP Labs: Advertise the Default Route
If you’re an Internet Service Provider running BGP with your customers, you might not want to send them the whole Internet routing table. Sending the regional prefixes and the default route is usually good enough.
FRRouting Claims IBGP Loopbacks Are Inaccessible
Last week, I explained the differences between FRRouting and more traditional networking operating systems in scenarios where OSPF and IBGP advertise the same prefix:
- Traditional networking operating systems enter only the OSPF route into the IP routing table.
- FRRouting enters OSPF and IBGP routes into the IP routing table.
- On all platforms I’ve tested, only the OSPF route gets into the forwarding table1.
One could conclude that it’s perfectly safe to advertise the same prefixes in OSPF and IBGP. The OSPF routes will be used within the autonomous system, and the IBGP routes will be propagated over EBGP to adjacent networks. Well, one would be surprised 🤦♂️
OSI Layers in Routing Protocols
Now and then, someone rediscovers that IS-IS does not run on top of CLNP or IP and claims that, therefore, it must be a layer-2 protocol. Even vendors’ documentation is not immune.
Interestingly, most routing protocols span the whole seven layers of the OSI stack, with some layers implemented internally and others offloaded to other standardized protocols.
netlab: Building Leaf-and-Spine Fabrics with the Fabric Plugin
netlab release 1.7.0 added the fabric plugin that simplifies building lab topologies with leaf-and-spine fabrics. All you have to do to build a full-blown leaf-and-spine fabric is:
- Specify the default device type
- Enable the fabric plugin
- Specify the number of leaves and spines in the fabric.
For example, the following lab topology builds a fabric with Arista cEOS containers having two spines and four leaves:
Worth Reading: Things We Know about Network Queues
Every time someone tries to persuade you to buy (expensive) big-buffer data center switches, take an antidote: the Things we (finally) know about network queues article by Avery Pennarun.
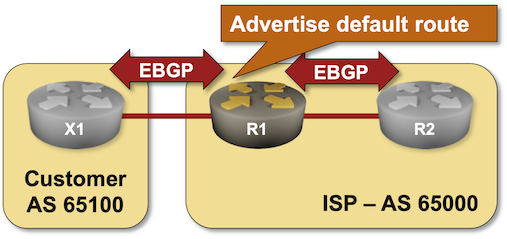
BGP Labs: Stop the Fat-Finger Incidents
Last time, we discussed the first line of defense against fat finger incidents: limiting the number of BGP prefixes your router accepts from a BGP neighbor. However, you can do much more without deploying customer-specific filters (which might require a customer database) or ROV/RPKI.
You can practice the default filters you should always deploy on EBGP sessions with your customers in the Stop the Propagation of Configuration Errors lab exercise.
FRRouting RIB and FIB
This is how we described the interactions between routing protocol tables, RIB, and FIB in the ancient times:
- Routing protocols compute the best paths to all known prefixes.
- These paths compete for entry in the routing table. The path(s) with the lowest administrative distance win.
- The entries from the routing table are fully evaluated (in particular, their next hops) and entered in the forwarding table.
Let’s use a simple BGP+OSPF network to illustrate what I’m talking about:
Interface EBGP Sessions on Arista EOS
Arista EOS and Cisco Nexus OS got interface EBGP sessions years after Cumulus Linux. While they’re trivially easy to configure on FRRouting (the routing daemon used by Cumulus Linux), getting them to work on Arista EOS is a bit tricky.
To make matters worse, my Google-Fu failed me when I tried to find a decent step-by-step configuration guide; all I got was a 12-minute video full of YouTube ads. Let’s fix that.
… updated on Friday, December 5, 2025 19:33 +0100
Running netlab and BGP Labs on Apple Silicon
I usually say that you cannot run netlab on Apple Silicon because the vendors don’t provide ARM images. However, when I saw an ARM version of the FRRouting container, I wondered whether I could run the BGP labs (admittedly only on FRR containers) on my M2 MacBook Pro.
TL&DR: Yes, you can do that.
Now for the recipe:
Worth Reading: History of Ethernet
The March 2024 Internet Protocol Journal has a lengthy article on the history and “future” of Ethernet that might be worth reading (although it’s short on details) if you weren’t around when it all started.
Video: Intro to Real Life Network Automation
Urs Baumann invited me to have a guest lecture in his network automation course, and so I had the privilege of being in lovely Rapperswil last week, talking about the basics of real-life network automation.
Urs published the video recording of the presentation on YouTube; hope you’ll like it, and if you don’t get too annoyed by the overly pushy ads, watch the other videos from his infrastructure-as-code course.
Data Center Fabric Designs: Size Matters
The “should we use the same vendor for fabric spines and leaves?” discussion triggered the expected counterexamples. Here’s one:
I actually have worked with a few orgs that mix vendors at both spine and leaf layer. Can’t take names but they run fairly large streaming services. To me it seems like a play to avoid vendor lock-in, drive price points down and be in front of supply chain issues.
As always, one has to keep two things in mind:
BGP AS Numbers for a Private MPLS/VPN Backbone
One of my readers was building a private MPLS/VPN backbone and wondered whether they should use their public AS number or a private AS number for the backbone. Usually, it doesn’t matter; the deciding point was the way they want to connect to the public Internet:
We also plan to peer with multiple external ISPs to advertise our public IP space not directly from our PE routers but from dedicated Internet Routers, adding a firewall between our PEs and external Internet routers.
They could either run BGP between the PE routers, firewall, and WAN routers (see BGP as High-Availability Protocol for more details) or run BGP across a bump-in-the-wire firewall:
OSPF Summarization and Split Areas
In the Do We Still Need OSPF Areas and Summarization? I wrote this somewhat cryptic remark:
The routers advertising a summarized prefix should be connected by a path going exclusively through the part of the network with more specific prefixes. GRE tunnel also satisfies that criteria; the proof is left as an exercise for the reader.
One of my readers asked for a lengthier explanation, so here we go. Imagine a network with two areas doing inter-area summarization on /24 boundary:
Cyber Crane Mesh Topology Built with netlab
Milan Zapletal submitted the source code for a huge lab topology they built with netlab. It has almost 50 routers and over 50 Linux nodes to emulate end-users and servers.
They used netlab to configure VLANs, VRFs, IS-IS, OSPF, EIGRP, BGP, MPLS, VXLAN, and EVPN. Imagine how long it would take to configure all that by hand using a more traditional labbing tool.
Worth Reading: Talent Gap in IT
If you need a good rant about Thought Leaders, Talent Gap, and Certification-Based-Hiring, look no further than I see a different gap from here!. Here’s a choice tidbit:
Every single job description that requires some sort of certification must be treated with suspicion. Demanding a certification usually means that you don’t know what you want, and you’re just outsourcing your thinking to someone else.
Have fun!
Worth Exploring: PCAP Analysis with Generative AI
John Capobianco published the source code of his Packet Buddy application on GitHub. It’s a Python UI that takes a PCAP file, converts it to JSON, and includes that JSON as part of the ChatGPT chat, allowing you to discuss the captured packets with ChatGPT.
His idea is one of the best uses of generative AI in networking I’ve seen so far, as long as you remember that you’re dealing with an overconfident intern who has no problem making up an answer just to sound smart. Have fun!
Finally, if you don’t want to use ChatGPT (I wouldn’t blame you) or send captured data into The Cloud, someone already adapted his idea to use local LLMs.
BGP Labs: Limit the Number of Accepted BGP Prefixes
Here’s an easy way to stop fat-finger incidents in which an end-user autonomous system redistributes IGP into BGP or advertises the whole DFZ routing table from affecting the entire Internet: limit the number of BGP prefixes your routers accept from your customers. You can practice this nifty feature in the next BGP lab exercise.
… updated on Thursday, March 7, 2024 16:05 +0100
Multiline Expressions in Ansible Playbooks
Another week, another Ansible quirk 🤷♂️ Imagine you have a long Jinja2 expression, and you want to wrap it into multiple lines to improve readability. Using multiline YAML format seems to be the ideal choice:
---
- name: Test playbook
hosts: localhost
tasks:
- set_fact:
a: >
{{ 123 == 345 or
123 > 345 }}
It works every time 50% of the time (this time depending on your Ansible version).
Rant: Multi-Vendor EVPN Fabrics
Daniel Dib tweeted about an old comment of mine a few days ago, adding1:
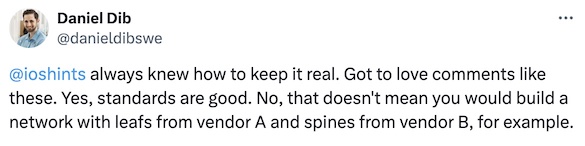
Not surprisingly, that was bound to upset a few people, and Roman Dodin quickly pointed out the EVPN interoperability tests:
netlab 1.8.0: Control-Plane Daemons, BIRD, dnsmasq
I wanted to include open-source networking-related software into netlab topologies since (at least) the days I was writing the DHCP relaying saga. It turned out to be a bit more complex than I anticipated (more about that in another blog post), but I hope you’ll find it useful. netlab release 1.8.0 includes dnsmasq running as a DHCP server and BIRD running OSPF and BGP. ExaBGP and GoBGP are already on the wish list; if you have any other ideas, please start a GitHub discussion.
I had a hard time finding reasonable container images for BIRD; the BIRD team does not publish them, and everything else I found looked either abandoned or a hobby project. The solution turned out to be exceedingly simple: you cannot run the containers without Docker anyway, which means the docker build command is just a few keystrokes away. I added Dockerfiles needed to build those containers to the netlab source code and implemented the netlab clab build command as a thin wrapper around docker build. It takes just a few seconds (plus the time it takes to download the Ubuntu container image) to build the containers you need.
Worth Reading: Unbloating the Buffers
In case you’ve heard about bufferbloat but don’t know what it is: Dan Groshev wrote a nice bufferbloat for dummies blog post on the APNIC blog.
netlab on Packet Pushers
A few weeks ago, Ethan Banks invited me to chat about netlab, and we had great fun discussing its intricacies for almost an hour. I also managed to win the Buzzword Bingo describing netlab as
Intent-based infrastructure-as-code digital twins lifecycle management system
The podcast was published a few days ago; listen to it on the PacketPushers website or YouTube.