Blog Posts in October 2023
Weird: vJunos Evolved 23.2R1.5 Declines DHCP Address
It’s time for a Halloween story: imagine the scary scenario in which a DHCP client asks for an address, gets it, and then immediately declines it. That’s what I’ve been experiencing with vJunos Evolved release 23.2R1.15.
Before someone gets the wrong message: I’m not criticizing Juniper or vJunos.
- Juniper did a great job releasing a no-hassles-to-download virtual appliance.
- DHCP assignment of management IPv4 address worked with vJunos Evolved release 23.1R1.8
- There were reports that the DHCP assignment process in vJunos Evolved 23.1R1.8 was not reliable, but it worked for me so far, so I’m good to go as long as I can run the older release.
- I might get to love vJunos Evolved. Boot- and configuration times are very reasonable.
However, it looks like something broke in vJunos release 23.2, and it would be nice to figure out what the workaround might be.
Worth Exploring: BGP from Theory to Practice
My good friend Tiziano Tofoni finally created an English version of his evergreen classic BGP from theory to practice with co-authors Antonio Prado and Flavio Luciani.
I had the Italian version of the book since the days I was running SDN workshops with Tiziano in Rome, and it’s really nice to see they finally decided to address a wider market.
Also, you know what would go well with that book? Free open-source BGP configuration labs of course 😉
Early Data-Link Layer Addressing
After covering the theoretical part of network addressing (part 2, part 3), let’s go into some practical examples. I’ll start with data link layer and then move on to networking and higher layers.
The earliest data link implementations that were not point-to-point links were multi-drop links and I mentioned them in the networking challenges part of the webinar. Initially, we implemented multi-drop links with modems, but even today you can see multi-drop in satellite communications, Wi-Fi, or in cable modems.
BGP Labs: Multivendor External Routers
Here’s a quick update on the BGP Labs project status: now that netlab release 1.6.4 is out, I could remove the dependency on using Cumulus Linux as the external BGP router.
You can use any device that is supported by bgp.session and bgp.policy plugins as the external BGP router. You could use Arista EOS, Aruba AOS-CX, Cisco IOSv, Cisco IOS-XE, Cumulus Linux or FRR as external BGP routers with netlab release 1.6.4, and I’m positive Jeroen van Bemmel will add Nokia SR Linux to that list.
If you’re not ready for a netlab upgrade, you can keep using Cumulus Linux as external BGP routers (I’ll explain the behind-the-scenes magic in another blog post, I’m at the Deep Conference this week).
For more details, read the updated BGP Labs Software Installation and Lab Setup guide.
netlab 1.6.4: Support for Multi-Lab Projects; More BGP Goodies
Features in netlab release 1.6.4 were driven primarily by the needs of my BGP labs project:
- bgp.session plugin (formerly known as ebgp.utils plugin) got support for BFD, passive BGP peers and remove-private-as option.
- bgp.policy plugin implements basic BGP routing policy tools, including per-neighbor weights, local preference and MED.
- You can enable external tools in user defaults and use default groups to create user- or project-wide groups in the defaults files.
- Version-specific lab topology files allow netlab to select a lab topology that is a best fit for the netlab release you’re running.
Numerous platforms already support the new BGP nerd knobs:
Video: History of BGP Route Leaks
I’ll be talking about Internet routing security at the Deep conference in a few days, and just in case you won’t be able to make it1 ;) here’s the first bit of my talk: a very brief history of BGP route leaks2.
Note: you’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
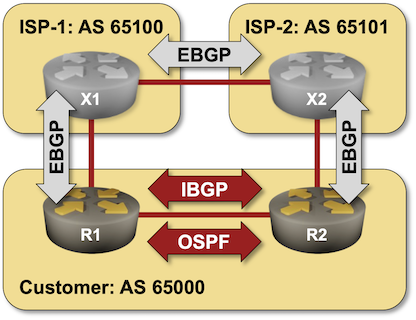
BGP Labs: Build Larger Networks with IBGP
After going through the BGP basics, it’s time to build a network that has more than one BGP router in it, starting with the simplest possible topology: a site with two WAN edge routers.
… updated on Thursday, November 2, 2023 10:36 UTC
Will Network Devices Reject BGP Sessions from Unknown Sources?
TL&DR: Violating the Betteridge’s Law of Headlines, the answer is “Yes, but the devil is in the details.”
It all started with the following observation by Minh Ha left as a comment to my previous BGP session security blog post:
I’d think it’d be obvious for BGP routers to only accept incoming sessions from configured BGP neighbors, right? Because BGP is the most critical infrastructure, the backbone of the Internet, why would you want your router to accept incoming session from anyone but KNOWN sources?
Following my “opinions are good, facts are better” mantra, I decided to run a few tests before opinionating1.
Worth Reading: AI Risks
Bruce Schneier wrote a thoughtful article on the various perceptions of AI Risks including this gem:
As the science-fiction author Ted Chiang has said, fears about the existential risks of AI are really fears about the threat of uncontrolled capitalism, and dystopias like the paper clip maximizer are just caricatures of every start-up’s business plan.
Enjoy!
BGP Labs: TCP-AO Protection of BGP Sessions
A few days after I published the EBGP session protection lab, Jeroen van Bemmel submitted a pull request that added TCP-AO support to netlab. Now that the release 1.6.3 is out, I could use it to build the Protect BGP Sessions with TCP Authentication Option (TCP-AO) lab exercise.
netlab 1.6.3: BGP Nerd Knobs
netlab release 1.6.3 added numerous BGP nerd knobs:
- You can create EBGP multihop sessions in the global routing table when using Arista EOS, Cisco IOSv, Cisco IOS-XE, FRR and Cumulus Linux 4.x.
- ebgp.utils plugin supports TCP-AO, configurable BGP timers, and Generic TTL Security Mechanism (TTL session protection)
- BGP neighbor reports hide irrelevant columns.
We also:
Worth Reading: Some Thoughts on Digital Twins
I encountered several articles explaining the challenges of simulating your network in a virtual lab in the last few months, including:
- Some thoughts on digital twins by Jeff McLaughlin
- Network Simulation is hard – Part 1, Part 2 – by Pete Crocker
- Twenty-five open-source network emulators and simulators you can use in 2023 by Brian Linkletter
Enjoy!
Worth Reading: Introduction of EVPN at DE-CIX
Numerous Internet Exchange Points (IXP) started using VXLAN years ago to replace tradition layer-2 fabrics with routed networks. Many of them tried to avoid the complexities of EVPN and used VXLAN with statically-configured (and hopefully automated) ingress replication.
A few went a step further and decided to deploy EVPN, primarily to deploy Proxy ARP functionality on EVPN switches and reduce the ARP/ND traffic. Thomas King from DE-CIX described their experience on APNIC blog – well worth reading if you’re interested in layer-2 fabrics.
Video: What Is Software-Defined Data Center
A few years ago, I was asked to deliver a What Is SDDC presentation that later became a webinar. I forgot about that webinar until I received feedback from one of the viewers a week ago:
If you like to learn from the teachers with the “straight to the point” approach and complement the theory with many “real-life” scenarios, then ipSpace.net is the right place for you.
I haven’t realized people still find that webinar useful, so let’s make it viewable without registration, starting with What Problem Are We Trying to Solve and What Is SDDC.
netlab 1.6.2: More Reporting Goodies
netlab release 1.6.2 improved reporting capabilities:
- BGP reports and IP addressing reports are fully IPv6-aware
- Some columns in BGP reports are optional to reduce the width of text reports
- You can filter the reports you’re interested in when using netlab show reports command
- Reports relying on ipaddr Ansible filter display warnings (instead of crashing) if you don’t have Ansible installed.
In other news:
- Stefano Sasso added support for ArubaOS-CX running within containerlab
- You can use inter-VRF route leaking with Cumulus Linux or FRR
BGP Labs: Route Aggregation
In the BGP Route Aggregation lab you can practice:
- OSPF-to-BGP route redistribution
- BGP route aggregation
- Suppression of more-specific prefixes in the BGP table
- Prefix-based filtering of outbound BGP updates
What Is Ultra Ethernet All About?
If you’re monitoring the industry press (or other usual hype factories), you might have heard about Ultra Ethernet, a dazzling new technology that will be developed by the Ultra Ethernet Consortium1. What is it, and does it matter to you (TL&DR: probably not2)?
As always, let’s start with What Problem Are We Solving?
BGP Session Security: Be Very Skeptical
A while ago I explained how Generalized TTL Security Mechanism could be used to prevent denial-of-service attacks on routers running EBGP. Considering the results published in Analyzing the Security of BGP Message Parsing presentation from DEFCON 31 I started wondering how well GTSM implementations work.
TL&DR summary:
Worth Reading: Flow Distribution Across ECMP Paths
Dip Singh wrote another interesting article describing how ECMP load balancing implementations work behind the scenes. Absolutely worth reading.
