Category: BGP
Explore and Fix BGP Wedgies
RFC 4264 defines BGP wedgies as “a class of BGP configurations for which there is more than one potential outcome, and where forwarding states other than the intended state are equally stable.” Even worse, “the stable state where BGP converges may be selected by BGP in a non-deterministic manner.”
Want to know more? You can explore a real-life BGP wedgie and fix it in the latest BGP lab exercise.
Looking for a Simple Multihop EBGP Use Case
I plan to add several challenge labs using multihop EBGP sessions to the BGP labs project, including:
- Running BGP between VMs and central BGP route servers
- Using multihop EBGP session to send full Internet routing table to a customer without overloading the PE-router
- Running EBGP EVPN session between loopbacks advertised with EBGP IPv4 session (🤢)
However, I would love to start with a simple use case to help engineers unfamiliar with BGP realize when they might have to use multihop EBGP sessions. Unfortunately, I can’t find one, and the scenarios where I used multihop EBGP in the past (EBGP load balancing and using a low-end router in the EBGP path, where I was effectively using the reverse application of #2 as a customer) are mostly irrelevant.
Would you have an easy-to-understand use case that is best solved with a multihop EBGP session? Please share it in the comments. Thanks a million!
Running BGP Labs in GitHub Codespaces
I love open-source tools (and their GitHub repositories). Someone launches a cool idea, and you can dig through their source code to figure out how it works. It beats reading documentation or fixing AI hallucinations every day of the week ;)
Not too long ago, the containerlab team launched the ability to run containerlab within a free1 container2 running on GitHub, and that seemed like a perfect solution to run the BGP labs (Jeroen van Bemmel pointing me in the right direction was another significant step forward).
Automated Validation of BGP Labs
In late 2023, I started playing with the idea of having automated validation in netlab. The early implementation was used in BGP labs, and a user liked it so much that he opened an issue saying:
I would suggest providing netlab validate for each lab.
Numerous rounds of yak-shaving later, I merged a humongous commit that adds automated validation to these lab exercises:
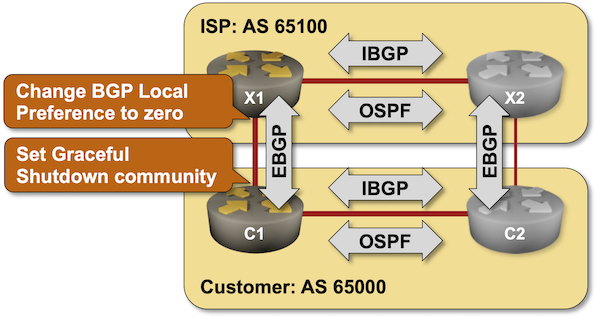
BGP Labs: Graceful Shutdown
Using the typical default router configurations, it can take minutes between a failure of an inter-AS link and the convergence of BGP routes. You can fine-tune that behavior with BGP timers and BFD (and still get pwned by Graceful Restart). While you can’t influence link failures, you could drain the traffic from a link before starting maintenance operations on it, and it would be a shame not to do that considering there’s a standard way to do that – the GRACEFUL_SHUTDOWN BGP community defined in RFC 8326. That’s what you’ll practice in the next BGP lab exercise.
BGP Route Reflectors Considered Harmful
The recent IBGP Full Mesh Between EVPN Leaf Switches blog post generated an interesting discussion on LinkedIn focused on whether we need route reflectors (in small fabrics) and whether they do more harm than good. Here are some of the highlights of that discussion, together with a running commentary.
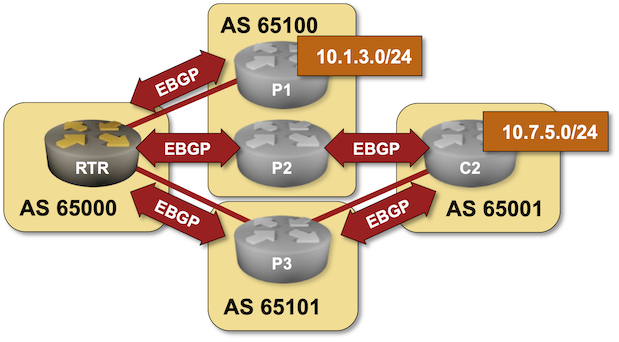
BGP Labs: Load Balancing across EBGP Paths
Let’s open another juicy can of BGP worms: load balancing. In the first lab exercise, you’ll configure equal-cost load balancing across EBGP paths and tweak the “What is equal cost?” algorithm to consider just the AS path length, not the contents of the AS path.
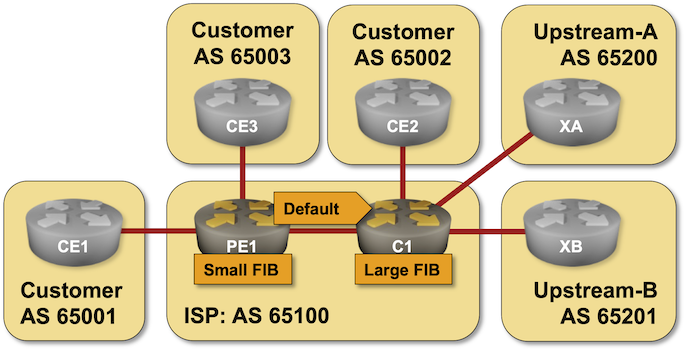
BGP Labs: Reduce FIB Size on Access Routers
Here’s another BGP lab challenge to start your weekend: use RIB-to-FIB filters to reduce the forwarding table size on access routers in a large Service Provider network.
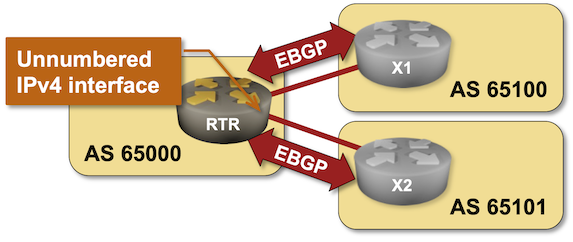
BGP Labs: EBGP Sessions over IPv6 LLA Interfaces
If you insist on building your network with EBGP as a better IGP, make sure your implementation supports running IPv4 and IPv6 address families over EBGP sessions established between IPv6 link-local addresses (the functionality lovingly called unnumbered EBGP sessions).
Want to practice that neat trick? Check out the EBGP Sessions over IPv6 LLA Interfaces lab exercise.
BGP Challenge: Build BGP-Free MPLS Core Network
Here’s another challenge for BGP aficionados: build an MPLS-based transit network without BGP running on core routers.
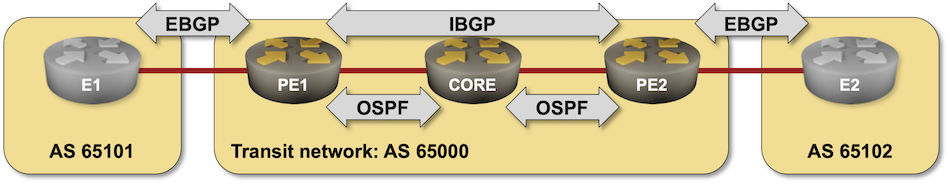
That should be an easy task if you configured MPLS in the past, so try to spice it up a bit:
- Use SR/MPLS instead of LDP
- Do it on a platform you’re not familiar with (hint: Arista vEOS is a bit different from Cisco IOS)
- Try to get it running on FRR containers.
Repost: EBGP-Mostly Service Provider Network
Daryll Swer left a long comment describing how he designed a Service Provider network running in numerous private autonomous systems. While I might not agree with everything he wrote, it’s an interesting idea and conceptually pretty similar to what we did 25 years ago (IBGP without IGP, running across physical interfaces, with every router being a route-reflector client of every other router), or how some very large networks were using BGP confederations.
Just remember (as someone from Cisco TAC told me in those days) that “you might be the only one in the world doing it and might hit bugs no one has seen before.”
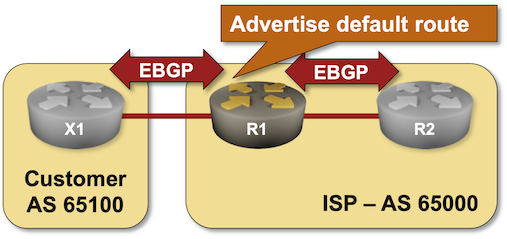
BGP Labs: Advertise the Default Route
If you’re an Internet Service Provider running BGP with your customers, you might not want to send them the whole Internet routing table. Sending the regional prefixes and the default route is usually good enough.
FRRouting Claims IBGP Loopbacks Are Inaccessible
Last week, I explained the differences between FRRouting and more traditional networking operating systems in scenarios where OSPF and IBGP advertise the same prefix:
- Traditional networking operating systems enter only the OSPF route into the IP routing table.
- FRRouting enters OSPF and IBGP routes into the IP routing table.
- On all platforms I’ve tested, only the OSPF route gets into the forwarding table1.
One could conclude that it’s perfectly safe to advertise the same prefixes in OSPF and IBGP. The OSPF routes will be used within the autonomous system, and the IBGP routes will be propagated over EBGP to adjacent networks. Well, one would be surprised 🤦♂️
BGP Labs: Stop the Fat-Finger Incidents
Last time, we discussed the first line of defense against fat finger incidents: limiting the number of BGP prefixes your router accepts from a BGP neighbor. However, you can do much more without deploying customer-specific filters (which might require a customer database) or ROV/RPKI.
You can practice the default filters you should always deploy on EBGP sessions with your customers in the Stop the Propagation of Configuration Errors lab exercise.
FRRouting RIB and FIB
This is how we described the interactions between routing protocol tables, RIB, and FIB in the ancient times:
- Routing protocols compute the best paths to all known prefixes.
- These paths compete for entry in the routing table. The path(s) with the lowest administrative distance win.
- The entries from the routing table are fully evaluated (in particular, their next hops) and entered in the forwarding table.
Let’s use a simple BGP+OSPF network to illustrate what I’m talking about:
