BGP Labeled Unicast Interoperability Challenges
Jeff Tantsura left me tantalizing hint after reading the BGP Labeled Unicast on Cisco IOS blog post:
Read carefully “Relationship between SAFI-4 and SAFI-1 Routes” section in RFC 8277
The start of that section doesn’t look promising (and it gets worse):
It is possible that a BGP speaker will receive both a SAFI-11 route for prefix P and a SAFI-42 route for prefix P. Different implementations treat this situation in different ways.
Now for the details:
netlab MPLS Support
netlab release 1.2.0 adds full-blown MPLS and MPLS/VPN support:
- VRF definitions and layer-3 VRFs
- VRF-aware OSPF, IS-IS and BGP
- Traditional MPLS with LDP (SR-MPLS was already available)
- BGP Labeled Unicast
- MPLS/VPN: VPNv4 and VPNv6 address family support
It’s never been easier to build full-blown MPLS/VPN labs ;)… if you’re OK with using Cisco IOS or Arista EOS. Please feel free to submit a PR to add support for other platforms.
You might want to start with the VRF tutorial to see how simple it is to define VRFs, and follow the installation guide to set up your lab – if you’re semi-fluent in Linux, the easiest option would be to run Arista cEOS.
Worth Reading: Higher Levels of Address Aggregation
Every now and then someone tells me how much better the global Internet would be if only we were using recursive layers (RINA) and hierarchical addresses. I always answer “that’s a business problem, not a technical one, and you cannot solve business problems by throwing technology at them”, but of course that has never persuaded anyone who hasn’t been running a large-enough business for long enough.
Geoff Huston is doing a much better job in the March 2022 ISP Column – read the Higher Levels of Address Aggregation, and if you still need more technical details, there’s 30+ pages of RFC 4984.
Worth Reading: Career Advice I'd Give to Younger Me
You MUST read the next masterpiece coming from Ethan Banks: Career Advice I’d Give To 20, 30 and 40-Something Year Old Me. I found this bit particularly relevant:
Your life is at least half over. Stop wasting time doing things other people think are important.
If only Ethan would have told me that wisdom ten years ago.
Video: Combining Data-Link- and Network Layer Addresses
The previous videos in the How Networks Really Work webinar described some interesting details of data-link layer addresses and network layer addresses. Now for the final bit: how do we map an adjacent network address into a per-interface data link layer address?
If you answered ARP (or ND if you happen to be of IPv6 persuasion) you’re absolutely right… but is that the only way? Watch the Combining Data-Link- and Network Addresses video to find out.
Is MPLS/VPN Too Complex?
Henk Smit made the following claim in one of his comments:
I think BGP-MPLS-VPNs are over-complicated. And you don’t get enough return for that extra complexity.
TL&DR: He’s right (and I just violated Betteridge’s law of headlines)
The history of how we got to the current morass might be interesting for engineers who want to look behind the curtain, so here we go…
Duplicate ARP Replies with Anycast Gateways
A reader sent me the following intriguing question:
I’m trying to understand the ARP behavior with SVI interface configured with anycast gateways of leaf switches, and with distributed anycast gateways configured across the leaf nodes in VXLAN scenario.
Without going into too many details, the core dilemma is: will the ARP request get flooded, and will we get multiple ARP replies. As always, the correct answer is “it depends” 🤷♂️
BGP Labeled Unicast on Arista EOS
A week ago I described how Cisco IOS implemented BGP Labeled Unicast. In this blog post we’ll focus on Arista EOS using the same lab as before:
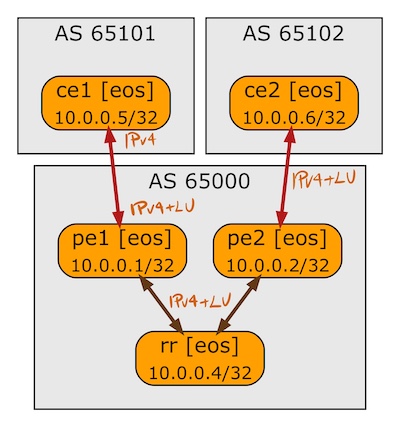
BGP sessions in the BGP-LU lab
… updated on Friday, May 31, 2024 13:51 +0200
Combining BGP and IGP in an Enterprise Network
Syed Khalid Ali left the following question on an old blog post describing the use of IBGP and EBGP in an enterprise network:
From an enterprise customer perspective, should I run iBGP, iBGP+IGP (OSPF/ISIS/EIGRP), or IGP with mutual redistribution on the edge routers? I was hoping you could share some thoughtful insight on when to select one over the other.
We covered many relevant details in the January 2022 Design Clinic; here’s the CliffNotes version. Remember that the road to hell (and broken designs) is paved with great recipes and best practices and that I’m presenting a black-and-white picture because I don’t feel like transcribing our discussion into an oversized blog post. People wrote books on this topic; search for “Russ White books” to find a few.
Finally, there’s no good substitute for understanding how things work (which brings me to another webinar ;).
Worth Reading: VMware Operations Guide
Iwan Rahabok’s open-source VMware Operations Guide is now also available in Markdown-on-GitHub format. Networking engineers support vSphere/NSX infrastructure might be particularly interested in the Network Metrics chapter.
Draw a Network Diagram from Excel Spreadsheet
Would you happen to have your network connectivity data in a tabular format (Excel or similar)? Would you like to make a graph out of that?
Look at the Excel-to-Graphviz solution created by and Salman Naqvi and Roman Urchin. It might not be exactly what you’re looking for, but you might get a few ideas and an inspiration to do something similar.
Video: Managed SD-WAN Services
Should service providers offer managed SD-WAN services? According to Betteridge’s law of headlines, the answer is NO, and that’s exactly what I explained in a short video with the same name.
Turns out there’s not much to explain; even with my usual verbosity I was done in five minutes, so you might want to watch SD-WAN Technical Challenges as well.
Beware: Ansible Reorders List Values in Loops
TL&DR: Ansible might decide to reorder list values in a loop parameter, resulting in unexpected order of execution and (in my case) totally borked device configuration.
A bit of a background first: I’m using an Ansible playbook within netlab to deploy initial device configurations. Among other things, that playbook deploys configuration snippets for numerous configuration modules, and the order of deployment is absolutely crucial. For example, you cannot activate BGP neighbors in Labeled Unicast (BGP-LU) address family (mpls module) before configuring BGP neighbors (bgp module).
BGP Labeled Unicast on Cisco IOS
While researching the BGP RFCs for the Three Dimensions of BGP Address Family Nerd Knobs, I figured out that the BGP Labeled Unicast (BGP-LU, advertising MPLS labels together with BGP prefixes) uses a different address family. So far so good.
Now for the intricate bit: a BGP router might negotiate IPv4 and IPv4-LU address families with a neighbor. Does that mean that it’s advertising every IPv4 prefix twice, once without a label, and once with a label? Should that be the case, how are those prefixes originated and how are they stored in the BGP table?
As always, the correct answer is “it depends”, this time on the network operating system implementation. This blog post describes Cisco IOS behavior, a follow-up one will focus on Arista EOS.
MPLS/LDP Creation Myths
Hannes Gredler wrote an interesting comment to my Segment Routing vs LDP in Hub-and-Spoke Networks blog post:
In 2014 when I did the first prototype implementation of MPLS-SR node labels, I was stunned that just with an incremental add of 500 lines of code to the vanilla IPv4/IPv6 IS-IS codebase I got full any-to-any connectivity, no sync issues, no targeted sessions for R-LFA …. essentially labeled transport comes for free.
Based on that, one has to wonder “why did we take the LDP detour and all the complexity it brings?”. Here’s what Hannes found out:
