Category: security
Worth Reading: Why Quantum Crypto is Bollocks
Today is a perfect day to point out the fantastic Why Quantum Cryptanalysis is Bollocks presentation (HT: A blog post by George Michaelson)
It’s a must-read, even if you’re absolutely uninterested in the topic. Just replace “Quantum mumbo-jumbo” with AI or SDN ;) Have fun!
Video: Internet Routing Security (DEEP 2023)
My Internet Routing Security talk from last year’s DEEP conference (a shorter version of the Internet Routing Security webinar) is now available on YouTube.
Hope you’ll find it useful ;)
Worth Reading: The Evolution of Network Security
Sharada Yeluri published an interesting overview of the evolution of network security, from packet filtering firewalls to GenAI and Quantum Computing (yeah, she works for a networking vendor ;). Definitely worth reading if you’re looking for an intro-level overview.
SR/MPLS Security Framework
A long-time friend sent me this question:
I would like your advice or a reference to a security framework I must consider when building a green field backbone in SR/MPLS.
Before going into the details, keep in mind that the core SR/MPLS functionality is not much different than the traditional MPLS:
Worth Reading: Cybersecurity Is Broken
Another cybersecurity rant worth reading: cybersecurity is broken due to lack of consequences.
Bonus point: pointer to RFC 602 written in December 1973.
Is BGP TTL Security Any Good?
After checking what routers do when they receive a TCP SYN packet from an unknown source, I couldn’t resist checking how they cope with TCP SYN packets with too-low TTL when using TTL security, formally known as The Generalized TTL Security Mechanism (GTSM) defined in RFC 5082.
TL&DR: Not bad: most devices I managed to test did a decent job.
Video: Outages Caused by Bugs in BGP Implementations
The previous BGP-related videos described how fat fingers and malicious actors cause Internet outages.
Today, we’ll focus on the impact of bugs in BGP implementations, from malformed AS paths to mishandled transitive attributes. The examples in the video are a few years old, but you can see similar things in the wild in 2023.
Open BGP Daemons: There's So Many of Them
A while ago, the Networking Notes blog published a link to my “Will Network Devices Reject BGP Sessions from Unknown Sources?” blog post with a hint: use Shodan to find how many BGP routers accept a TCP session from anyone on the Internet.
The results are appalling: you can open a TCP session on port 179 with over 3 million IP addresses.
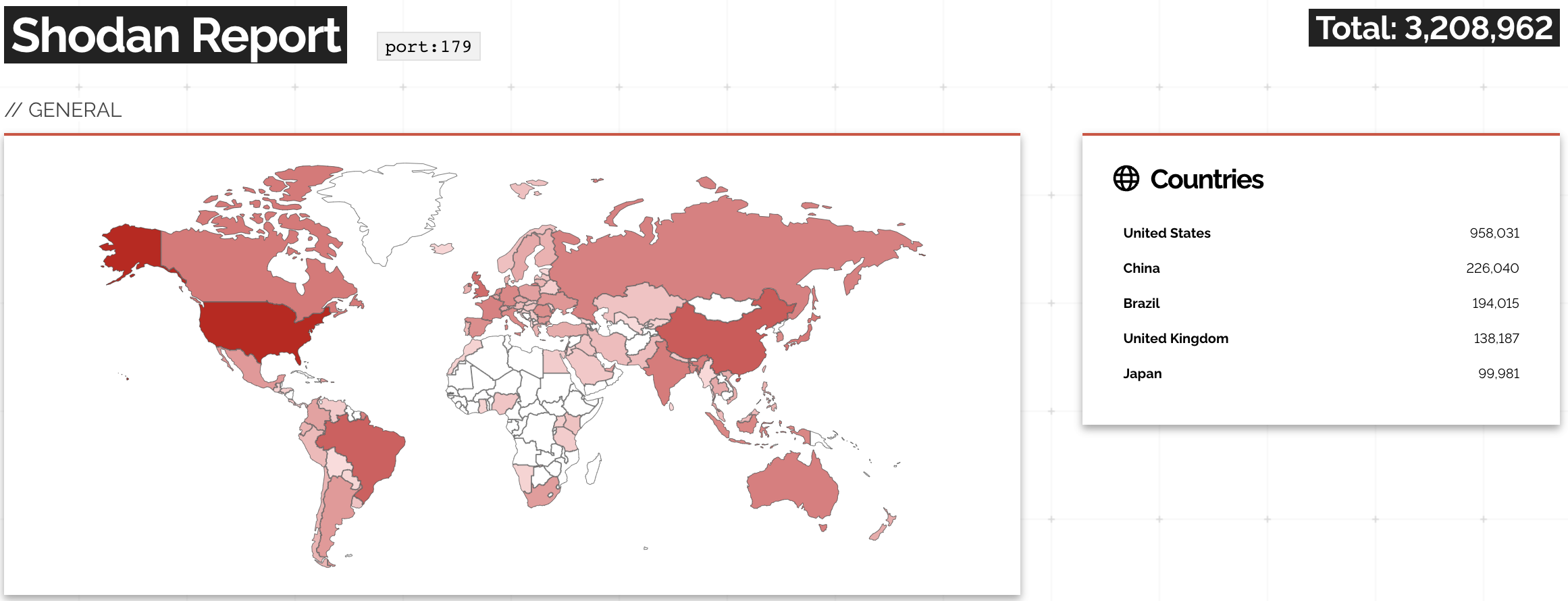
A report on Shodan opening TCP session to port 179
… updated on Wednesday, November 15, 2023 19:38 UTC
Rapid Progress in BGP Route Origin Validation
In 2022, I was invited to speak about Internet routing security at the DEEP conference in Zadar, Croatia. One of the main messages of the presentation was how slow the progress had been even though we had had all the tools available for at least a decade (RFC 7454 was finally published in 2015, and we started writing it in early 2012).
At about that same time, a small group of network operators started cooperating on improving the security and resilience of global routing, eventually resulting in the MANRS initiative – a great place to get an overview of how many Internet Service Providers care about adopting Internet routing security mechanisms.
Video: Hacking BGP for Fun and Profit
At least some people learn from others’ mistakes: using the concepts proven by some well-publicized BGP leaks, malicious actors quickly figured out how to hijack BGP prefixes for fun and profit.
Fortunately, those shenanigans wouldn’t spread as far today as they did in the past – according to RoVista, most of the largest networks block the prefixes Route Origin Validation (ROV) marks as invalid.
Notes:
- ROV cannot stop all the hijacks, but it can identify more-specific-prefixes hijacks (assuming the origin AS did their job right).
- You’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
Video: History of BGP Route Leaks
I’ll be talking about Internet routing security at the Deep conference in a few days, and just in case you won’t be able to make it1 ;) here’s the first bit of my talk: a very brief history of BGP route leaks2.
Note: you’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
… updated on Thursday, November 2, 2023 10:36 UTC
Will Network Devices Reject BGP Sessions from Unknown Sources?
TL&DR: Violating the Betteridge’s Law of Headlines, the answer is “Yes, but the devil is in the details.”
It all started with the following observation by Minh Ha left as a comment to my previous BGP session security blog post:
I’d think it’d be obvious for BGP routers to only accept incoming sessions from configured BGP neighbors, right? Because BGP is the most critical infrastructure, the backbone of the Internet, why would you want your router to accept incoming session from anyone but KNOWN sources?
Following my “opinions are good, facts are better” mantra, I decided to run a few tests before opinionating1.
BGP Session Security: Be Very Skeptical
A while ago I explained how Generalized TTL Security Mechanism could be used to prevent denial-of-service attacks on routers running EBGP. Considering the results published in Analyzing the Security of BGP Message Parsing presentation from DEFCON 31 I started wondering how well GTSM implementations work.
TL&DR summary:
Random Thoughts on Zero-Trust Architecture
When preparing the materials for the Design Clinic section describing Zero-Trust Network Architecture, I wondered whether I was missing something crucial. After all, I couldn’t find anything new when reading the NIST documents – we’ve seen all they’re describing 30 years ago (remember Kerberos?).
In late August I dropped by the fantastic Roundtable and Barbecue event organized by Gabi Gerber (running Security Interest Group Switzerland) and used the opportunity to join the Zero Trust Architecture roundtable. Most other participants were seasoned IT security professionals with a level of skepticism approaching mine. When I mentioned I failed to see anything new in the now-overhyped topic, they quickly expressed similar doubts.
Please Respond: MANRS Customer Survey
Andrei Robachevsky asked me to spread the word about the new MANRS+ customer survey:
MANRS is conducting a survey for organizations that contract connectivity providers to learn more about if and how routing security fits into their broader supply chain security strategy. If this is your organization, or if it is your customers, we welcome you to take or share the survey at https://www.surveymonkey.com/r/BDCWKNS
I hope you immediately clicked on the link and completed the survey. If you’re still here wondering what’s going on, here’s some more information from Andrei:
