Update: workaround for sluggish CB-QoS MIB
More than a year ago, I wrote about the very slow update rate of the variables in the CB-QoS MIB. In August WB found a workaround (do a show policy-map interface before reading the counters) and now Jared has tested it and confirmed that it works. He’s configured a simple EEM applet that executes the show command once per second:
event manager applet UpdateMibTables
event timer watchdog time 1
action 1.0 cli command "enable"
action 2.0 cli command "show policy-map int dialer0"
With this fix, he can use the SNMP variables in other EEM applets to detect VoIP calls within 1-2 seconds.
Don’t forget: numerous EEM topics are described in the Embedded Event Manager (EEM) workshop. You can attend an online version of the workshop; we can also organize a dedicated event for your networking team.
IPv6 CPE router requirements
It’s almost unbelievable: more than 10 years after the IPv6 specs have been completed, someone finally realized it would be a good idea to specify the minimum requirements for a decent IPv6 CPE router. While this document will not solve the lack of low-cost IPv6-ready CPE devices, it’s definitely a step in the right direction, more so as it clearly acknowledges the need for DHCPv6 (some people still believe SLAAC is the solution to every problem ever invented).
Here are a few highlights from the document:
IP over DWDM
A while ago I was pushed (actually it was a kind nudge) into another interesting technology area: optical networks, with emphasis on IP over DWDM. I realized almost immediately that I’d encountered another huge can of worms. A few issues you can stumble across when trying to plug routers or switches directly into DWDM networks are documented in my IP over dense wave division multiplexing (DWDM): Metro and core issues article recently published by SearchTelecom.com.
Cloud computing and public transport
Greg Ferro has republished an older post in which he compares Cloud Computing with public transport (and notes that nothing has changed in more than a year since he wrote the original article). His analogy is more than fitting; a perfect example is Google’s new Google Docs offering, where Stephen Foskett did a nice cost analysis of the unsupported service as compared to supported one.
I’m describing aspects of cloud computing in its various incarnations in my Next-generation IP Services workshop. You can attend an online version of the workshop or we can organize a dedicated event for your team.
Translated into public transport terms: if you want to fly cheap, choose Ryan Air (in Google’s case, you pay 25 cents per gigabyte per year); if you want reasonable support and flexibility, use Lufthansa ($3.50 per gigabyte per year for Google Apps Premier Edition customers or 14 times more than the unsupported capacity).
If you’re unhappy with my choice of airlines, insert your own selection in the above paragraph ;)
NAT-PT is totally broken in late IOS releases
When the current variant of IPv6 was selected 15 years ago, seamless integration with IPv4 was a big deal, resulting in NAT-PT architecture. NAT-PT tried to solve too many problems and (as I pointed out in my IPv6 Deployment workshop), while the 6to4 NAT is manageable, the 4to6 NAT is horrific (NAT64 and DNS64 are more reasonable; more about them in an upcoming post).
NAT between IPv4 and IPv6 hosts is just one of the topics covered in the Enterprise IPv6 Deployment workshop. You can attend an online version of the workshop or we can organize a dedicated event for your team.
To make matters worse, the NAT-PT implemented in Cisco IOS is totally broken due to removal of fast switching support in IOS release 12.4(20)T and numerous other releases. As I wrote a year and a half ago, removing fast switching will bite us eventually … and so it does when you try to use NAT-PT.
Rant: The long-term consequences of book piracy
A few hours after I’ve published my review of the “Cisco routers for the desperate” book someone posted a link to a digital (pirated) copy of the book to my Facebook page, no doubt feeling like a hero fighting for the freedom of information (or some similar nonsense).
I didn’t even try to download the book to see whether it was a leaked copy from the publisher (in which case someone has some serious problems) or a scanned PDF.
Weird GPRS and UMTS latency
Bad designer sent me an interesting comment: 2G and 3G networks have huge latency issues. GPRS is intolerable, UMTS is awful and HSPDA is reasonable but still not what one would hope for.
The latency does not seem to be associated with serialization delay. UMTS gives you reasonable transfer rates and significant latency and GPRS gives you an order of magnitude higher latency than ISDN with comparable transfer rate. If anyone knows enough about the mobile technologies to explain this phenomenon (or at least give me useful pointers) I’d really appreciate your comments.
ITU and Internet Billing: It’s a Déjà-Vu All Over Again
My friend Stretch alerted me to an article published by BBC News, which reports that “an EU cyber security expert” told “a House of Lords committee” (wow, that’s the perfect body to deal with Internet issues) that the proposal submitted by Chinese to an ITU-T study group required “modifications to BGP” which would “threaten the stability of the entire Internet.”
Regardless of whatever the original proposal has been, the information has been distorted, twisted, adapted, abstracted, and misunderstood so many times before being published that it’s impossible to figure out what exactly has been going on. The account of an eyewitness (sitting in the Kampala talks in September) doesn’t tell much more.
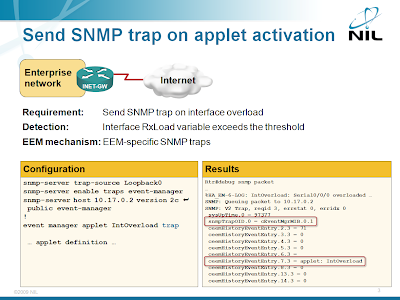
Send a SNMP trap from an EEM applet
The engineer who wanted to detect specific DoS attack (WAN link overload) with EEM applet asked for something more in his original question: he wanted to receive a SNMP trap on the NMS when the DoS attack is detected. Implementing this requirement with an EEM applet is simple; you just need to add the trap keyword to the event manager applet configuration command.
EEM-SNMP integration is described in the Embedded Event Manager (EEM) workshop. You can attend an online version of the workshop; we can also organize a dedicated event for your networking team.
Next-generation IP services
A while ago I’ve created a short presentation describing modern IP- and web-based services. It describes the application-layer topics I’ve been focusing on in the last few years, from cloud computing to web-based applications. I've tried to keep it simple enough that someone without the prior knowledge of the field would not get lost after two slides, but still far away from high-level marketing nonsense (you can get plenty of that anywhere else). Today I finally found some time to spend on the paperwork and wrote the description of the Next-generation IP Services tutorial.
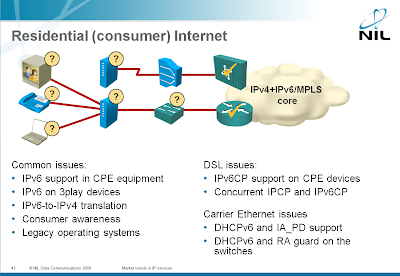
IPv6 is not ready for residential deployment
The main driver for IPv6 deployment is the IPv4 address space exhaustion, caused primarily by fast growth of residential users.
Each residential user needs an IP address, a small company doesn’t need anything more and even a reasonably-sized company can survive with a few IP addresses.
One would expect the vendor readiness to follow this pattern, but the situation is just the opposite: while the enterprise networking devices have pretty good IPv6 support (Data Center components from some vendors are a notable exception), the vendors serving the residential market don’t care.
The Service Provider-related IPv6 challenges are covered in my Market trends in Service Provider networks workshop. You can attend a web-based tutorial version or we can organize a dedicated workshop event for your team.
HQF: Truly Hierarchical Queuing
After doing the initial tests of the HQF framework, I wanted to check how “hierarchical” it is. I’ve created a policy-map (as before) allocating various bandwidth percentages to individual TCP/UDP ports. One of the classes had a child service policy that allocated 70% of the bandwidth to TCP and 30% of the bandwidth to UDP (going to the same port#), with fair queuing being used in the TCP subclass.
Short summary: HQF worked brilliantly.
Book review: Cisco Routers for the Desperate
If you happen to be one of those “universal engineers” tasked with configuring a Cisco router just because you deployed a web site yesterday, you’re probably already searching for a book in the Dummies series. Once your desperation exceeds a certain threshold, you might consider the “Cisco Routers for the Desperate”.
The idea is great: give someone who hasn’t seen Cisco IOS CLI before enough knowledge to perform the basic tasks. The writing style is surprisingly good and the book is filled with well-explained printouts you might get from the router. Looks like a perfect book for the task … if only it wouldn’t be hopelessly outdated.
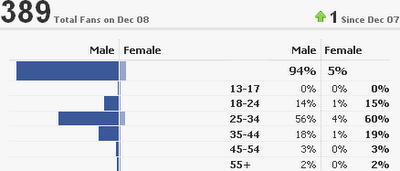
The sorry state of our industry
One of the few benefits of having a Facebook page is the ability to view the fan statistics (Facebook calls that Insights). I’ve just looked at the gender demographics of my fans and I was astounded; nothing has changed in the last 20 years. What are we doing wrong?
Load Sharing 101 (with References)
It looks like my load sharing posts did not paint the whole picture; I’m always assuming the readers have a basic level of IP routing knowledge (somewhere around BSCI/CCNP) and jump into juicy details. Let’s try to fix this error and start from the beginning. For more details, watch the How Networks Really Work webinar.
A router receives its routing information (reachability of IP prefixes) from various sources: connected IP prefixes, static routes and dynamic routing protocols. For every IP prefix, the best source (= one with the lowest administrative distance) is selected and only the route(s) from that source are included in the IP routing table.