… updated on Wednesday, November 15, 2023 19:38 UTC
Rapid Progress in BGP Route Origin Validation
In 2022, I was invited to speak about Internet routing security at the DEEP conference in Zadar, Croatia. One of the main messages of the presentation was how slow the progress had been even though we had had all the tools available for at least a decade (RFC 7454 was finally published in 2015, and we started writing it in early 2012).
At about that same time, a small group of network operators started cooperating on improving the security and resilience of global routing, eventually resulting in the MANRS initiative – a great place to get an overview of how many Internet Service Providers care about adopting Internet routing security mechanisms.
In September 2022, I took the list of Tier-1 providers from Wikipedia1, did a quick search on the MANRS Network Operator Participants page, and came up with this slide2:
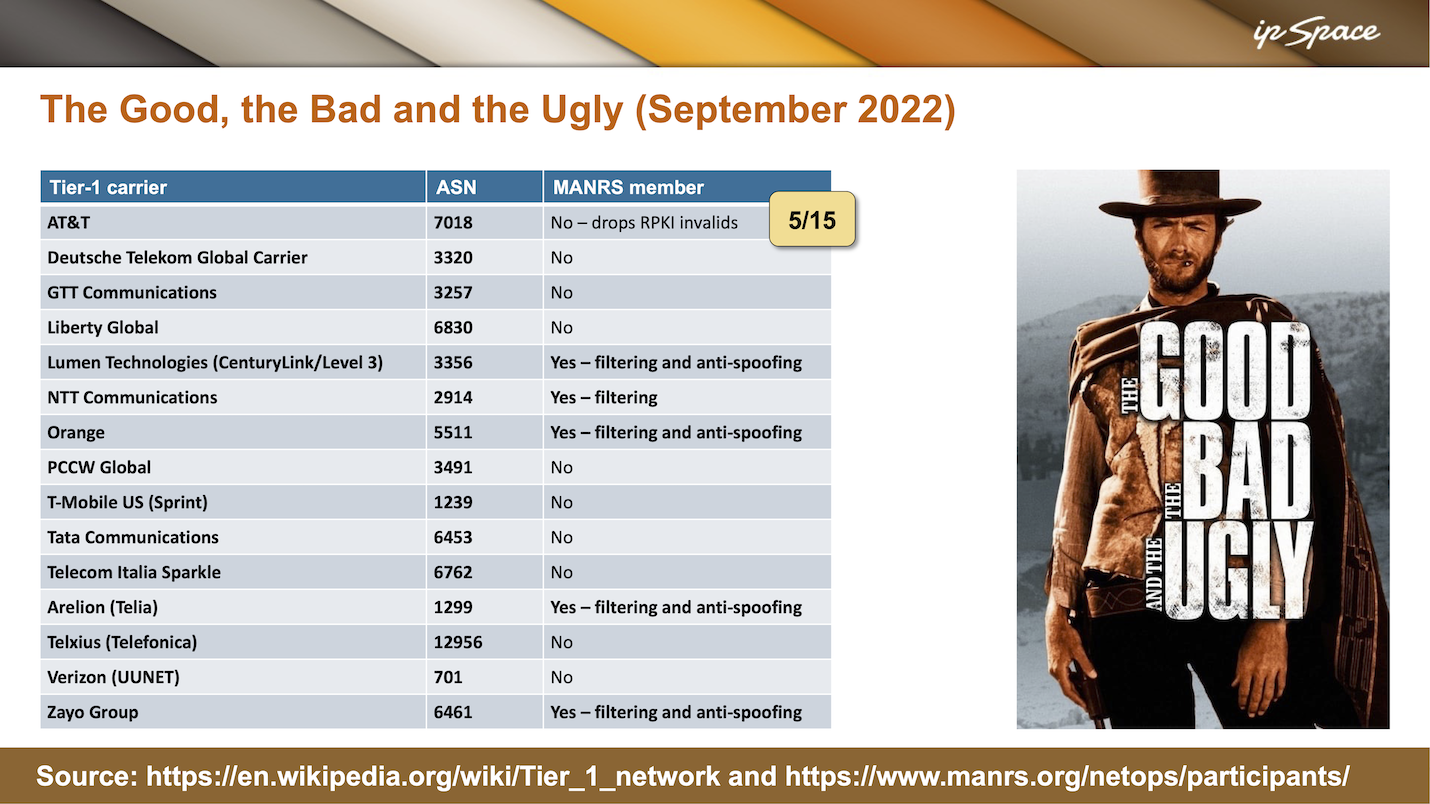
I wasn’t able to make it to Zadar – I got COVID-19 a few days before the conference started – but I did turn the presentation into a webinar. As I delivered the webinar in April 2023, I updated that same slide, and the progress made in half a year was remarkable. I was also a bit skeptical that large organizations managed to make so much progress in such a short time.
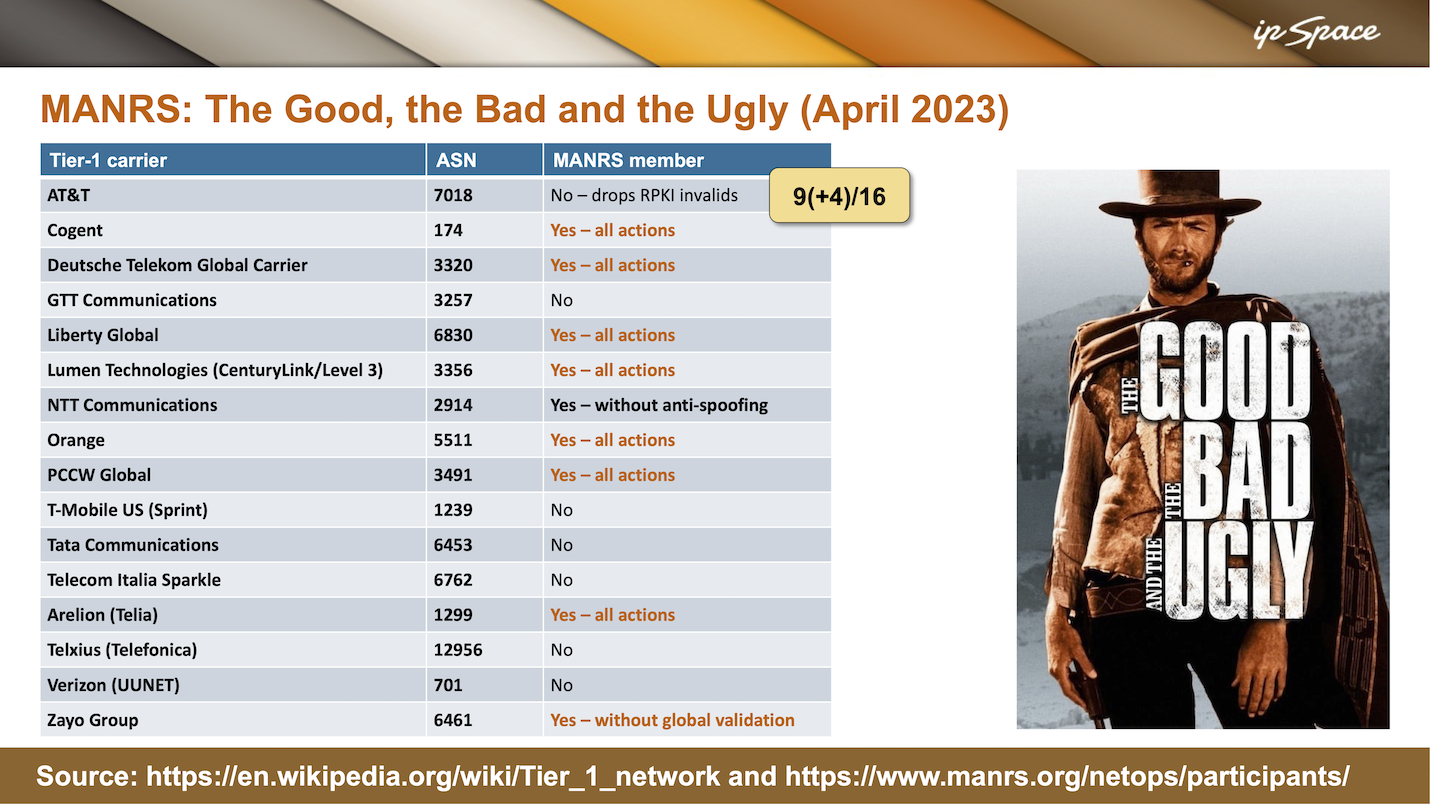
The organizers of the DEEP conference were kind enough to invite me to have the same presentation this year, and of course, I updated that same slide. In the meantime, MANRS started measuring how thorough the ISPs were in signing their prefixes (RPKI) and registering them in the Internet Routing Registry (IRR), making the data more meaningful than just the “I claim I do all of that” declarations I had been skeptical about back in April.
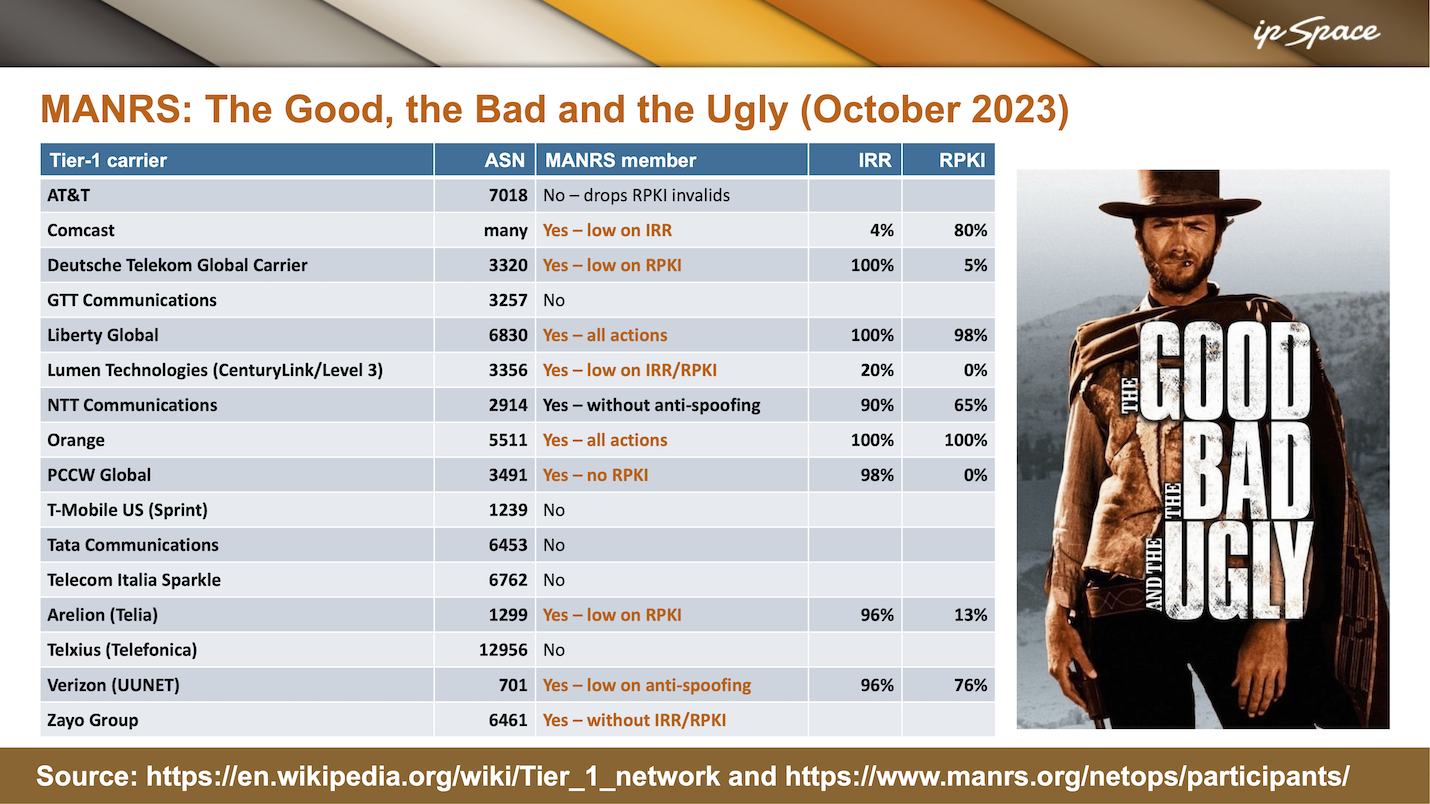
A recent MANRS blog post delivered the icing (and the cherry) on the cake – a group of academics managed to measure how well individual autonomous systems use Route Origin Validation (ROV) to block invalid prefixes. Almost all tier-1 service providers they were able to measure got the perfect score:
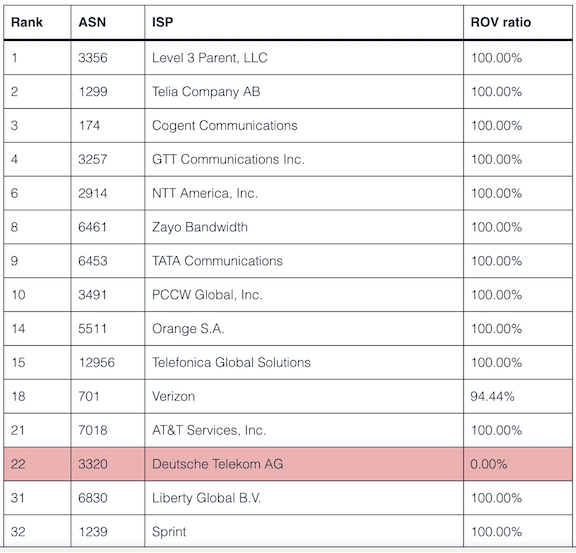
Even better: ROV adoption at the tier-1 level shields the autonomous systems using those tier-1 providers from distant shenanigans. However, it obviously cannot protect customers of a regional ISP from bogus announcements created in the same region.
If you want to know how well ROV protects end users, check out the work done by Geoff Huston and his team. They are using Cloudflare RPKI beacons (meaning the destination is always close to the end-user) and doing measurements from the web browsers. Here’s their view of the worldwide ROV adoption:
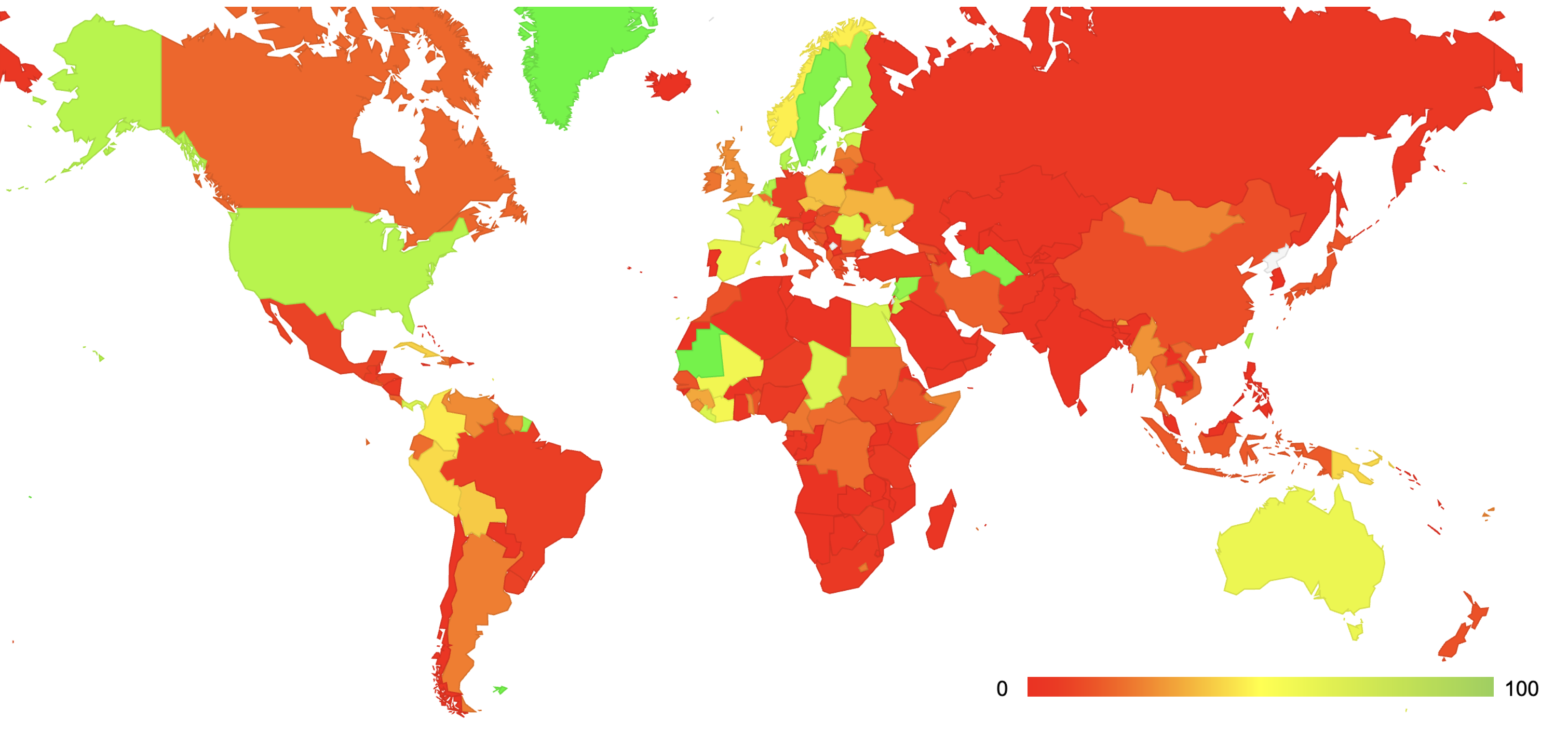
Worldwide ROV adoption (from potaroo.net)
Now for some bad news: as is evident from the above map, the future is not evenly distributed. As I was preparing yet another BGP security presentation for an Italian conference, I used the results of the RoVista measurement tool to see whether Italian ISPs perform Route Origin Validation3, and the results were dismal:
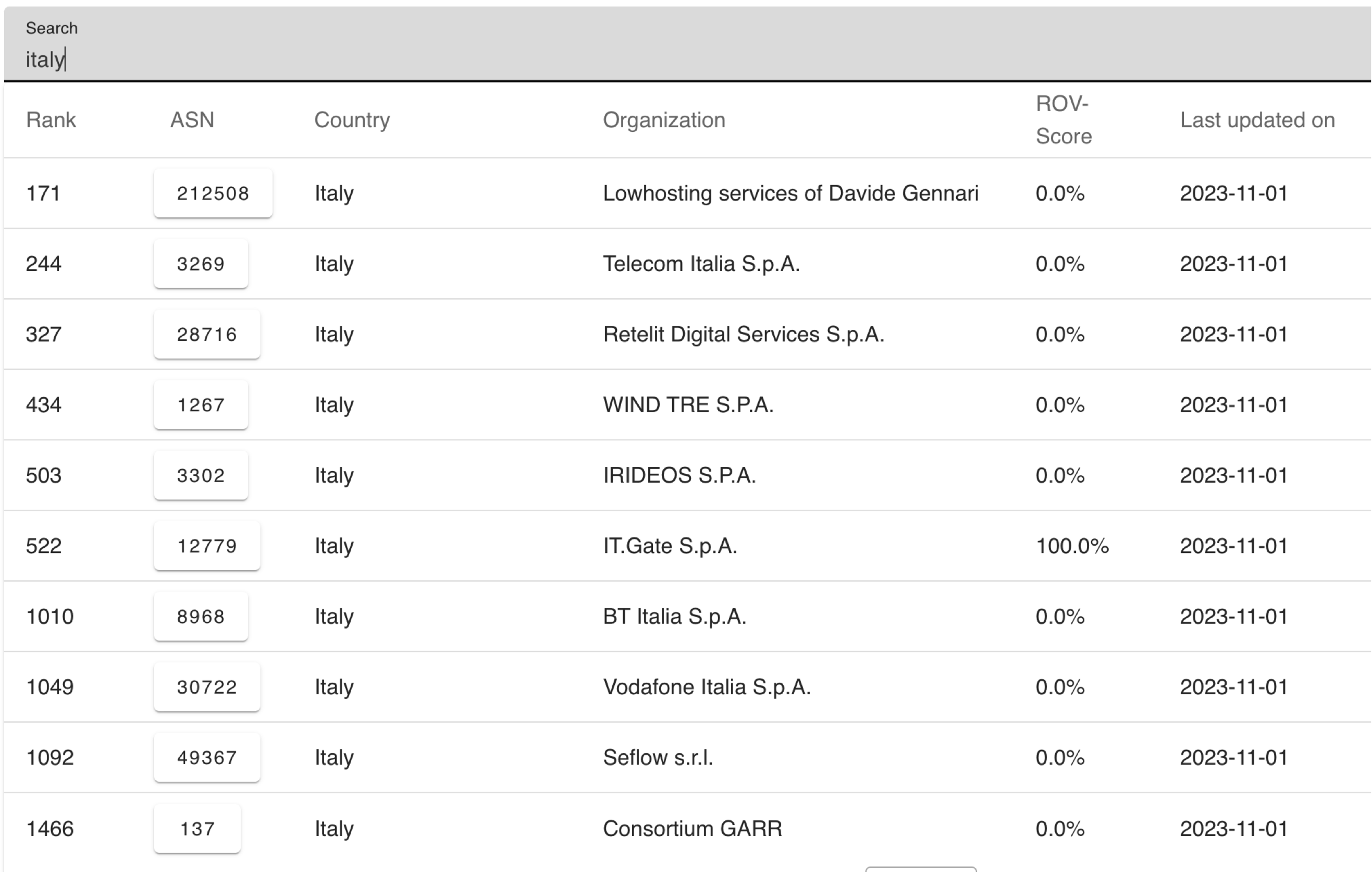
Plenty of work still needs to be completed before we have secure and resilient Internet routing.
-
Please note that the Wikipedia list of tier-1 providers is changing over time. Fortunately, you can view the history of changes. ↩︎
-
Click the slide to get a larger picture ↩︎
-
Please note I’m not picking on Italian ISPs; I just wanted to show locally relevant data. We’d probably get similar results for most countries. ↩︎
