… updated on Tuesday, March 11, 2025 13:48 +0100
VLAN Interfaces and Subinterfaces
Early bridges implemented a single bridging domain across all ports. Within a few years, we got multiple bridging domains within a single device (including bridging implementation in Cisco IOS). The capability to have multiple bridging domains stretched across several devices was still missing… until the modern-day Pandora opened the VLAN box and forever swamped us in the complexities of large-scale bridging.
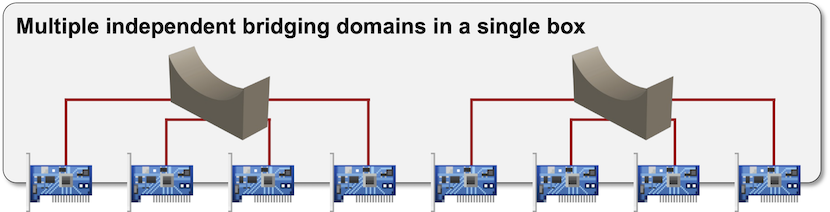
Multiple bridging domains in a single box
VLANs were first introduced in bridges and followed the usual “keep things simple, just plug it in and pray” mentality. You could assign a port to a VLAN (access port) or filter VLANs on a trunk port.
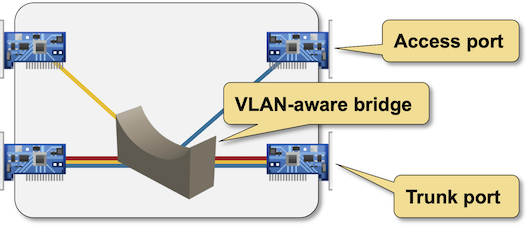
VLAN-aware bridges
Layer-3 switches added VLAN interfaces (logical interfaces representing the whole bridging domain), resulting in the configuration model used on modern layer-3 switches when configuring switchport on an interface.
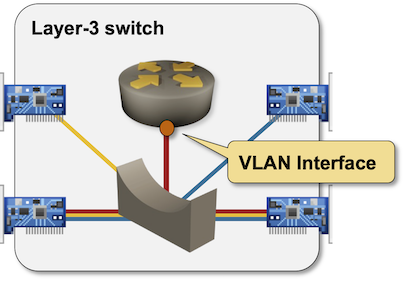
VLAN interface (for red VLAN) in a layer-3 switch
The first router-focused VLAN use case was a router on a stick – a device with a single physical interface that had to forward network-layer packets between VLANs. Routers always performed packet forwarding between interfaces; the typical device configuration model followed that paradigm and introduced VLAN subinterfaces – a logical interface receiving all packets belonging to a single VLAN that arrive through the parent physical interface.
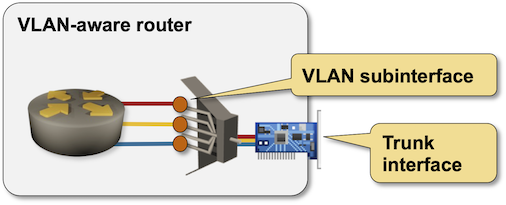
VLAN-aware router with a VLAN trunk interface
Linux networking supports both concepts. The VLAN interfaces used in the switch configuration model map pretty well into Linux bridges (a virtual interface-like object to which other interfaces are connected). The VLAN subinterface used in router configurations maps into a Linux VLAN interface (a child interface of a particular physical interface).
You can configure multi-VLAN bridging on Linux with a set of Linux bridges or a VLAN-aware Linux bridge. You have to configure VLAN (sub)interfaces to per-VLAN Linux bridges or use VLAN trunks and access interfaces with the VLAN-aware bridge.
You can explore both options with netlab; it uses per-VLAN bridges for FRRouting nodes and a VLAN-aware bridge for Cumulus Linux 4.x (Cumulus Linux 5.x configures a VLAN-aware bridge with NVUE).
The different implementations of these configuration models resulted in hilarious headaches:
- Layer-3 switches like Arista EOS or Cisco Nexus OS have a split personality. They can behave like a router (with VLAN subinterfaces) or a switch (with VLAN interfaces) simultaneously, but you cannot combine the two on the same physical interface.
- You would configure Cisco routers running Cisco IOS completely differently than Cisco switches running the same operating system.
- Cisco IOS routers still use the ancient bridge groups and Bridge Virtual Interface. To implement VLAN bridging, you must create VLAN subinterfaces and assign them to bridge groups.
- To ensure you remain thoroughly confused, Cisco IOS XE uses Bridge Domain Interfaces instead of Bridge Virtual Interfaces.
What else would you expect to get from an industry that firmly believes in recycling old code and doing more with less?
Next: Routed Interfaces on Layer-3 Switches and Internal VLANs Continue
Revision History
- 2025-03-11
- Added diagrams
- Introduced the two Linux deployment models
