Security in Leaf-and-Spine Fabrics
One of my readers sent me an interesting question:
How does one impose a security policy on servers connected via a Clos fabric? The traditional model of segregating servers into vlans/zones and enforcing policy with a security device doesn’t fit here. Can VRF-lite be used on the mesh to accomplish segregation?
Good news: the security aspects of leaf-and-spine fabrics are no different from more traditional architectures.
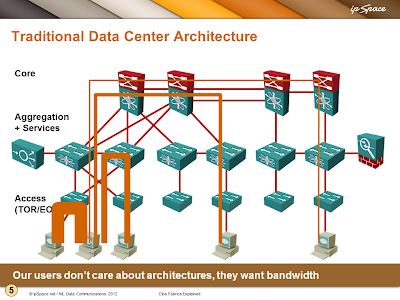
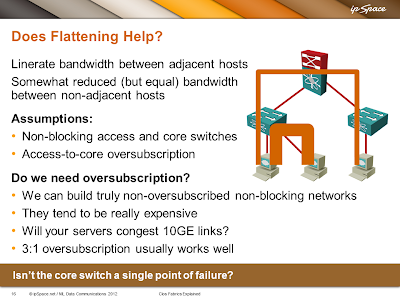
Leaf-and-spine (or Clos) architecture is just a pretty optimal way of connecting switches in a fabric that results in equidistant endpoints. Here are two slides from my Clos Fabric Explained webinar that illustrate the difference.
As long as the leaf nodes have the ability to spread the traffic across all uplinks, leaf-and-spine architecture can implement layer-2 or layer-3 networks. Layer-2 leaf-and-spine architectures may be limited to two spine nodes (in a VSS/vPC/MC-LAG cluster) unless you’re deploying one of the layer-2 ECMP technologies (Trill, FabricPath, VCS Fabric, SPB…).
You can also implement a mixed layer-2+layer-3 leaf-and-spine network with layer-3 forwarding implemented in the core switches (using any variant of multi-node FHRP) or across all leaf switches.
I would strongly recommend using layer-3 leaf-and-spine fabric with overlay virtual networks on top of it, but that’s a different story.
Connecting a security device to a leaf-and-spine fabric is no different from connecting a security device to a traditional data center network – you have to pull multiple VLANs (or VRFs) to the ToR switch to which the security device is connected.
I would virtualize the security device and connect it to overlay virtual networks, but yet again, that’s a different story.
Summary: You don’t have to learn any new tricks to implement security in leaf-and-spine fabrics. Use whatever worked for you in the past.
Need more details?
The Clos Fabrics Explained webinar contains a detailed explanation of numerous leaf-and-spine designs including:
- Non-redundant layer-3 design;
- Layer-3 design with multihomed servers;
- Layer-2-only design without server-to-switch LAG (ideal for vSphere deployments);
- Layer-2 design with server-to-switch LAG;
- Mixed L2/L3 design with L3 forwarding on spine switches;
- Mixed L2/L3 design with L3 forwarding on leaf switches.
If you need even more details, ExpertExpress might be the simplest alternative.

Can you also cover how security device in a clos network be connected in your webinar.I dont find this in your leaf spine architecture webinar