Send a SNMP trap from an EEM applet
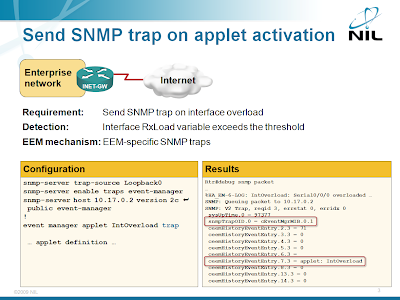
The engineer who wanted to detect specific DoS attack (WAN link overload) with EEM applet asked for something more in his original question: he wanted to receive a SNMP trap on the NMS when the DoS attack is detected. Implementing this requirement with an EEM applet is simple; you just need to add the trap keyword to the event manager applet configuration command.
EEM-SNMP integration is described in the Embedded Event Manager (EEM) workshop. You can attend an online version of the workshop; we can also organize a dedicated event for your networking team.
The SNMP trap contains the trap OID set to cEventMgrMIB.0.1. The .1 suffix indicates the trap was sent by the EEM server not by applet/Tcl policy code. The rest of the trap data is a copy of an EEM history event table object. One of the fields (ceemHistoryEventType1) contains an index into the event description table, another field (ceemHistoryPolicyName) the name of the EEM applet that triggered the trap.

event manager applet VrfDown
event syslog occurs 1 pattern "%BGP-5-ADJCHANGE: neighbor.*vpn vrf.*Down.*"
action 010 set neighIp "none"
action 011 set neighVrf "none"
action 012 set ifname "none"
action 013 set ifDesc "none"
action 014 info type routername
action 100 regexp "([0-9]+\.[0-9]+\.[0-9]+\.[0-9]+)" "$_syslog_msg" neighIp
action 101 regexp "(vrf\ VPN_[A-Z]+\ )" "$_syslog_msg" neighVrf
action 102 cli command "show ip route $neighVrf $neighIp | include , via"
action 103 regexp "directly connected,\ via\ (.*)\r" "$_cli_result" match ifName
action 104 cli command "show interface $ifName | include Description:"
action 105 regexp "Description: (.*)\r" "$_cli_result" match ifDesc
action 200 puts "$ifName DOWN ($ifDesc)"
action 201 snmp-trap strdata "EEM detected $ifName DOWN ($ifDesc) on $_info_routername"