Blog Posts in April 2008
The Impact of tx-ring-limit
Setting the size of the hardware output queue in Cisco IOS with the (then undocumented) tx-ring-limit (formerly known as tx-limit) has been a big deal when I was developing the first version of the QoS course that eventually became the initial release of the Implementing Cisco Quality of Service training.
However, while it's intuitively clear that the longer hardware queue affects the QoS, years passed before I finally took the time to measure the actual impact.
Display operational IPv6 interfaces
PE-A#show ipv6 interface brief | section up
Serial1/0 [up/up]
unassigned
Serial1/1 [up/up]
FE80::C800:CFF:FEA7:0
Loopback0 [up/up]
unassigned
The definition of the associated follow-up lines depends on the printout. Usually the indented lines are assumed to belong to a section, but you might be surprised.
What Is CLNS?
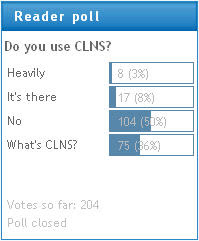
According to the results of my recent Do you use CLNS poll, around 10% of my readers use CLNS in their network, while 36% of them wonder what that acronym stands for.
Let's start with the acronyms. CLNS (Connection-Less Network Service) in combination with CLNP (Connection-Less Network Protocol) is the ISO (International Standards Organization) equivalent to IP.
MAC addresses on VLAN interfaces
Almost-Dynamic Routing over ADSL Interfaces
Recently I had to implement Internet access using ADSL as the primary link and ISDN as the backup link. Obviously the most versatile solution would use the techniques described in my Small Site Multi-homing articles, but the peculiarities of Cisco IOS implementation of the ADSL technology resulted in a much simpler solution.
IOS implementation of PPPoE links uses dialer interfaces. However, the “dialing” on these interfaces is activated as soon as the underlying PPPoE session is active (before the first interesting packet is routed to the interface). When the simulated dial-out occurs, the router starts PPP negotiations including the IPCP handshake, which usually results in an IP address assigned to the dialer interface. Net result: if the dialer interface has an IP address, the PPPoE session is obviously active (and vice versa).
Hot air party
However, what really prompted me to start writing this post was the "wisdom" spread by industry journalists. Network world was still moderate; the gentleman at LinuxWorld had some strong opinions. It would be OK if they would stop at bashing the new module (and questioning the value-for-price is always fair), but of course it's more fun being all over the place, evangelizing the beauties of PC-based open-source routers and the demise of traditional router vendors. While there's (yet again) nothing wrong with open-source, let's bring a bit of the history into the picture:
- 15 years ago, someone had a great idea to install WAN cards and routing software into PC servers. The journalists greeted that idea as the downfall of dedicated routers. Guess what ... it flopped and the router market continued to grow.
- Cheap Layer-3 switches have been greeted as the next router killer. We still have routers and switches in our networks.
- People have been using Linux as their home firewalls for years ... and it hasn't really impacted the low-end router market; SOHO users are still preferring to buy Linksys (or whatever other cheap low-end brand) over configuring firewall on Linux.
- Public-domain BGP implementations have been around for as long as I can remember and they are not bad. Some people with very low budget use them for route servers ... but Cisco and Juniper are still selling high-end boxes.
In the real world of networks that have more than a few routers, if you have enough budget to buy yourself a good night's sleep, you usually install dedicated routing hardware ... but I guess this is not the sort of story that would sell the industry journals.
Interesting posts
A few interesting posts found on the Internet:
OSPFv3 Router ID: the Long Shadow of IPv4
One of the obscure facts about IPv6 OSPF (OSPFv3) is that it uses a 32-bit router ID like OSPFv2. It’s a reasonable choice; I have yet to see an OSPF network with over a billion routers. However, could you guess how this requirement is implemented in Cisco IOS? OSPFv3 searches for an IPv4 address (effectively the same algorithm used by OSPFv2) to get the router ID for the IPv6 routing process. Neat, isn’t it?
You might wonder what happens if you want to configure an IPv6-only router. OSPF won’t start unless you configure the router ID manually. And, no, you cannot enter a number (which would be the expected format, as the router ID is just a number in the IPv6 world); you have to enter an IPv4 address. Long live IPv4 :))
Subnet Masks in OSPF Network Statements
In a comment to my recent NTP-related post mentioning OSPF configuration, Wan Tajuddin correctly stated that the OSPF network statement should contain the wildcard bits, not the subnet mask. However, I was positive I had running networks with the network 0.0.0.0 0.0.0.0 area 0 OSPF configuration, so it was time for one more lab test. As it turns out, Cisco IOS started accepting either the wildcard bits or the subnet mask in the network OSPF configuration command.
Technology Is Supposed to Be Simple, Right?
In his comment to the one of my NTP articles, Joe said:
This is part of the problem with NTP. It's way more complicated then it needs to be. You shouldn't have to understand so much of it to use it on your routers. Take a look at openntpd. It's free and runs on bsd or linux.
I have to disagree with him on several counts:
BGP Essentials: Non-transit AS
One of the first things you have to do when configuring BGP with your ISP is to ensure you won’t become a transit AS. Decent ISPs filter out things that don’t belong to you from your updates, but not everyone cares (including some really big names), and so small organizations manage to bring down large parts of the Internet just with a few fat fingers.
Here’s the BGP configuration you should use on Cisco IOS: apply AS-path access-list to outbound updates with neighbor filter-list command:
Use UDP flood to increase router's CPU load
If you want to test the ERM policies in a controlled environment, it's almost mandatory to have tools that allow you to overload the router. One way to overload a router is to flood it with UDP packets. Flooding a router's IP address, you're guaranteed to raise the CPU to 100%, with majority of the process CPU being used by the IP Input process (the interrupt CPU load will also be significant).
This phenomenon illustrates very clearly why it's so important to have inbound access lists protecting the router's own IP addresses on all edge interfaces.
Do bootcamps make sense?
My recent post about a CCNP bootcamp program I was involved with generated interesting comments, most of them focusing on the question: “Does it make sense to attend a bootcamp?”
The answer depends on how you got to the stage where you want to (or need to) attain the CCxP certification. Before going into discussions on “experience” versus “knowledge retention” (potentially “aided” by brain dumps), please read The Top 10 Problems with IT Certification in 2008 article published by InformIT. My potential disagreements with this article are so minor that I will not even try to document them.
OK, now that we're on the same page, let's analyze why someone would want to pursue CCxP certification:
- To increase the salary or have better job options (as HR departments ask for people with specific set of certifications). From what I hear, this reason is more viable in US than the rest of the world (in most of Europe we can still test the technical skills of the candidates in any way we want without running the risk of being sued). Bootcamps might not be the best option for these candidates, as they tend to be priced similarly to the regular classes. Reading books or e-learning material (not to mention certain not-so-very-legitimate activities) will get you through the exams as long as they don't have the hands-on part ... and of course you'll end up having certification with zero experience;
- To learn something new and valuable resulting in a formal recognition of the effort. Don't even think about attending the bootcamps. If you're learning completely new concepts, go through the regular courses (or use e-learning combined with hands-on lab exercises). Highly intensive format of the bootcamps (after all, we're trying to squeeze almost two weeks worth of material into a single week) will fly way over your head.
- To formalize your experience ... either because you want to or because your employer needs certified head count (very common with Cisco partners trying to get better discount based on their partner status). In this case, a condensed bootcamp is usually the best option. For example, we had very successful bootcamp program a few years ago running back-to-back with the exams ... and, mind you, we used no cheating or brain dumps, the fact that the students took the exam right after the course obviously helped.
Last but definitely not least, it's worth mentioning that not all five-day courses have five days worth of content. In these cases, condensing them into bootcamps makes even more sense.
RFC 3514 implemented by the ASR series of routers
The RFC 3514 requires the end host to participate in the process, but as most operating system vendors still don't have a trusted computing platform, a transparent proxy has to be implemented on the network edges to properly tag the ingress packets. ASR 1000 has the first high-speed implementation of the RFC 3514 proxy thanks to its non-deterministic parallel QuantumFlow processors.
The configuration of the RFC 3514 proxy is extremely simple: all you need to do is to configure auto-secure mark on the ingress interfaces of the ASR 1000. Once the security bit has been set, you can use the match ip security-bit 0|1 command in a class-map or a route-map on any router running IOS release 12.4(11)T or later (the command is still hidden).
