Packet Filters on a Nexus 7000
We’re always quick to criticize ... and usually quiet when we should praise. I’d like to fix one of my omissions: a few days ago I was trying to figure out whether Nexus 7000 supports IPv6 access lists (one of the presentations I was looking at while researching the details for my upcoming Data Center webinar implied there might be a problem) and was pleasantly surprised by the breadth of packet filters offered on this platform. Let’s start with a diagram.
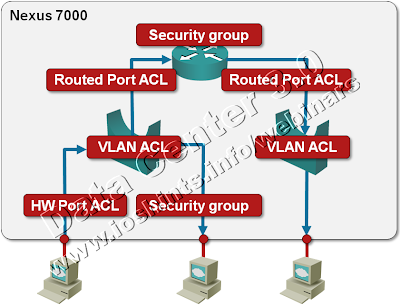
Every packet traversing a Nexus 7000 goes through a number of filters:
Inbound port filters. You can specify IPv4, IPv6 and MAC filters.
VLAN filters. Whenever a packet is bridged within a VLAN, vlan access-map is applied. VLAN access maps can match on IPv4, IPv6 and MAC addresses (using already-defined access-lists) and even redirect a packet to another interface for further analysis. VLAN filters can be applied to a range of VLANs to improve configuration scalability.
Obviously this step is skipped if the inbound interface is a layer-3 interface.
Routed port ACL. Whenever a packet enters or exits the layer-3 forwarding engine, it can be filtered with inbound/outbound ACL. Yet again, both IPv4 and IPv6 ACL are supported. If the packet is forwarded between two VLANs, the destination VLAN filter is also applied.
TrustSec Security Group. Last but not least, every packet traversing the Nexus 7000 is checked by TrustSec security group ACL (SGACL).
I would love to go into so many details in my Data Center 3.0 for Networking Engineers webinar (buy a recording or yearly subscription) but it’s quite impossible due to timing constraints and the breadth of technologies we’re covering. The “further reading” list that's part of the webinar materials should help you find in-depth information on the topics discussed in the webinar.