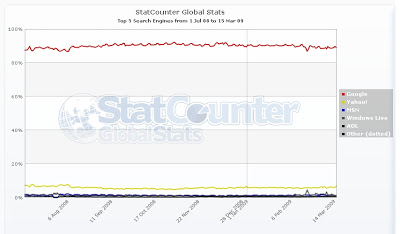
Off-topic: Search engine wars are over
As you can see, Google has approximately 90% market share, Yahoo (the second place) has less than 10%, the others are clearly irrelevant.
Recovering from expired one-time username
A reader sent me an interesting question:
Do you have any advice for resetting/logging into a router (2821) where the one time user of cisco:cisco has already been used?
I couldn't offer any better advice than performing the regular password recovery procedure. Is there another solution?
This article is part of You've asked for it series.
EBGP Load Balancing with a Multihop EBGP Session
Multihop EBGP sessions are the traditional way to implement EBGP load balancing on parallel links. EBGP session is established between loopback interfaces of adjacent routers (see the next diagram; initial router configurations are included at the bottom of the article) and static routes (or an extra instance of a dynamic routing protocol) are used to achieve connectivity between loopback interfaces (BGP next-hops). The load balancing is an automatic result of the recursive route lookup of BGP next hops.
Fat finger follow-up: use the key labels
Karsten Iwen made an interesting comment to my “Don't let a lab rat anywhere near a production box” post: you should avoid the SSH/VPN key generation mistakes by using key labels. He also wrote a post explaining the concept but since it’s in German, let me rephrase it in English.
Cisco IOS release 12.2(8)T added the label parameter to the crypto key generate rsa command. You can use this parameter to assign a label to your VPN key, for example
Rtr(config)#crypto key generate rsa label VPN modulus 2048
To use the labeled key to generate your certificate, use the rsakeypair command in the CA-trustpoint configuration mode:
crypto pki trustpoint example.com
enrollment retry count 100
enrollment mode ra
enrollment url http://ca.example.com/certsrv/mscep/mscep.dll
rsakeypair VPN
Build a VPN Across Your IP Network with Multi-VRF Feature
One of our customers had to provide end-to-end IP transport across their enterprise network for an outsourced video surveillance solution. We implemented a true VPN solution for them (the hosts in the enterprise network cannot access the surveillance equipment and vice versa) using the Multi-VRF feature available in all recent Cisco IOS releases.
I described the solution Add a VPN to an Enterprise Network with Multi-VRF Functionality article; you’ll find it somewhere in this list.
Are you willing to talk about SP infrastructure optimization?
Don't let a lab rat anywhere near a production box
I tried to do a few simple NETCONF tests yesterday (I wanted to see how the router's configuration looks like when it's encoded in XML). I didn't want to start a lab for such a simple task and decided to use my home router. SSH was the only reasonable transport (you can't run BEEP with standard Linux tools), but it was not working on the router.
Obviously I've configured too many lab devices in the past. As soon as I've realized I had SSH problems, my fingers automatically typed crypto key generate rsa. A few milliseconds after I've hit ENTER it dawned on me that my router uses PKI certificates for the VPN connection to our network ... and I've managed to invalidate the router's certificate, which is one of the few things that a reload will not solve. Although our IT guru was fantastic and approved my (router's) certificate request late in the evening, I still felt bad about the whole experience.
And the moral? Don't let a lab wizard with fast fingers too close to a production box :)
Off-topic: Marketing 2.0
 It's almost guaranteed to be a winning combination in a Bullshit Bingo.
It's almost guaranteed to be a winning combination in a Bullshit Bingo.
Generating syslog messages from Tcl
If you use Tcl to write Embedded Event Manager policies, you could use the action_syslog command to generate syslog messages. In all other Tcl-based environments (including tclsh), this API is not available, but you could use the syslog: file system to generate debugging messages.
Four byte AS number support in Cisco IOS
Last week IOS release 12.4(24)T appeared on CCO. One of the significant improvements in that release (I can’t manage to get enthusiastic about new kludges to support the SIP morass) is the support for 4-byte BGP AS numbers.
Finally an enterprise network that uses Cisco routers to connect to the Internet can use the new AS numbers distributed by the regional registries (assuming you’re brave enough to run 12.4(24)T on your production gear). The Service Providers using 7600 routers will have to wait … corresponding 12.2SR release is not yet available.
Hat tip to Tassos @ CCIE in 3 months: he was the first to write about this feature.
… updated on Monday, December 7, 2020 11:12 UTC
BGP AS-Path Prepending: Technical Details
I thought I knew all there is to know about the AS-path prepending before the February 2009 incident, which prompted me to focus on this particular Cisco IOS feature.
For example, did you know you could do inbound AS-path prepending? I didn’t, until Rodney Dunn from Cisco mentioned it in an e-mail exchange. Did you ever wonder whether the AS-path prepending affects inbound or outbound AS-path filters? I had a hunch it doesn’t, but was never sure. Time to figure out all the gory details…
AS-path incident: the bowdlerizer strikes
A post by CiscoSubnet has pointed me to the official IntelliShield alert describing the AS-path incident. While the alert is very well written (I wouldn’t expect less) and the associated Protecting Border Gateway Protocol for the Enterprise is excellent, I was highly amused by the following text:
Cisco Security Intelligence Operations has identified a method through which administrators can modify device configurations to mitigate the effects of the AS path processing issue. Administrators can limit the amount of AS path segments that are associated with any route by using the bgp maxas-limit feature …
The bgp maxas-limit command was suggested by some members of the NANOG mailing list as early as few hours after the incident (which happened on February 16th; the IntelliShield alert has been released on February 20th) and I’ve released a detailed article on February 17th. I know Cisco’s engineers did a great job in this particular case; why did someone have to run their results through the /usr/local/marketese | /usr/bin/bowdlerize?
Simulations in certification tests
Anyone who has ever had the “privilege” of interviewing a certified individual with purely theoretical knowledge appreciates the value of hands-on tests. The creators of certifications in the IT industry (including Cisco Systems) have responded by including more and more hands-on exercises in the certification exams. Unfortunately, Cisco decided not to use the real equipment, but rather simulations. While this is definitely better than relying exclusively on multiple-choice tests, students can still work their way through the simulations without having a decent level of hands-on experience.
Connecting a switch to itself: does it hurt?
I’ve got an unusual question a few days ago:
Does a loop (cable returning back to same switch) in one switch affect other switches? How can I detect that there is such a problem in a particular switch?
The correct answer to the first question is obviously it depends. To start with, it depends on whether the two ports will be able to communicate. With a crossover (switch-to-switch) cable (and assuming there are no negotiation issues), the physical layer will work correctly. If you’re using a standard RJ-45 patch cable, you’re “out of luck” unless the switch is too smart and has auto-MDI sensing (like the Linksys switches, now well hidden under obscure part numbers like Cisco SRW248G4). In this case, the two ports will become active even connected with a patch cable.
Online network diagram drawing tool
Andrew Yourtchenko invested “a few evenings” (his choice of words) and produced an online diagram drawing tool. There’s only one word to describe it: amazing.
I guess Andrew appreciates if you’d use the offline copy after you’ve tested the tool (otherwise we might overload his hosted account).