Exercise: Fix BGP Route Leaks
I created a netlab topology you can use to practice BGP security tools I described in the Internet Routing Security webinar:
- The lab topology mirrors the sample topology I described in the Classification of BGP Route Leaks (RFC 7908) blog post with one router per autonomous system
- BGP is configured on all devices, and EBGP sessions are set up between all directly-connected devices.
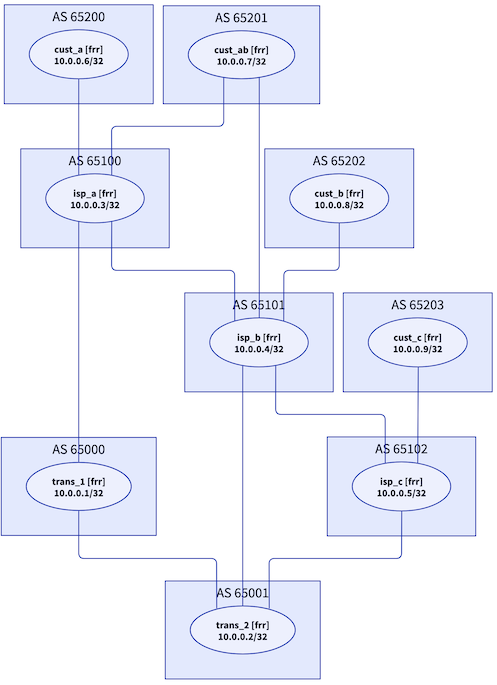
Lab topology (unfortunately turned around)
Autonomous systems advertise prefixes from three address ranges:
| AS type | Address range |
|---|---|
| Transit providers | 172.16.0.0/16 |
| Regional ISPs | 172.17.0.0/16 |
| Customers | 172.18.0.0/16 |
I also created a custom configuration template that reflects a typical ISP setup:
- Customer routes have BGP local preference 200. It’s always best to send traffic over links someone else is paying for.
- Peer routes have BGP local preference 150. It’s better to send traffic over zero-settlement links than over links where we have to pay for transit.
- Routes received from transit providers have default local preference. They are used only when we have no customer- or peer routes to a destination.
While you can use the lab with any supported device, I created the custom configuration template for FRR containers, Cumulus Linux, and Arista EOS.
I did not configure any BGP route filters, so you’ll get tons of “simple” route leaks from customers and peers, giving you plenty of opportunity to figure out how to stop them. On top of that:
- One of the customers announces way too many prefixes (a customer shall not advertise more than two prefixes)
- Another customer is advertising an internal prefix from the 10.0.0.0/8 block
- The third customers is advertising a prefix that belongs to an ISP (you’ll notice the same prefix is advertised as belonging to two different autonomous systems).
- An ISP is advertising a /25 prefix that should not be propagated in the global Internet
Fix the lab routing with BGP filters, do not change the route advertisements.
Running the Lab
The optimal way to run the lab is with Linux containers:
- Create a Ubuntu VM and use netlab installation scripts to install all the software you need. Please note that you don’t need nested virtualization if you run network devices as containers.
- Optional: download and install Arista cEOS container
- Download the topology file from GitHub into an empty directory.
- Start the lab with netlab up
- Enjoy!

1) Will there be a prize (e. g. giveaway) to win for solving the exercise? :D
2) Will there be a solution published after some time?
3) What are the smallest hardware requirements to run the lab?
1) 😂
2) Yes, I plan to write a series of blog posts covering various aspects of BGP security. Based on my past performance it might take a long while...
3) 2GB of RAM and 2 vCPU should be good enough. More in another blog post
looks easy. Just do what is done in real world and everything will be fine:
So a few filter policies and correct local-preference will "simulate" real life ISP behavior. Of course, you didn't provide any RIPE-like database to determine peering or upstream/downstream relationships.
Of course it's easy, which makes it even more annoying that so many people can't be bothered to get it right 🤷♂️