Blog Posts in December 2006
Configuration rollback fails completely with IP SLA
Per-destination or per-packet CEF load sharing?
To configure per-packet load-sharing, use the ip load-sharing per-packet interface configuration command (default is per-destination). This command has to be configured on all outgoing interfaces over which the traffic is load-shared.
The switch between the load-sharing modes is not immediate; sometimes you have to wait a few seconds for the ip load-sharing command to take effect, worst case a manual clearing of the CEF table (clear ip cef address) is required.
Configuration Change Logging ignores the configuration downloads
 The Configuration Change Notification and Logging feature is supposed to log changes to the router's configuration. While it does a great job of logging commands entered in the router configuration mode, it completely ignores configuration changes due to configuration download (for example, with configure network or copy tftp running-config command).
The Configuration Change Notification and Logging feature is supposed to log changes to the router's configuration. While it does a great job of logging commands entered in the router configuration mode, it completely ignores configuration changes due to configuration download (for example, with configure network or copy tftp running-config command).
Which switching path does an IOS feature use
I've got an excellent question recently: Which switching path is used in Zone-based firewalls when a packet is dropped? As usual, IOS documentation was not very helpful (which is understandable as the answer might depend on hardware platform, interface encapsulation, other features configured on the router etc.). However, there is a great tool to use - the show interface stats command.
Fine-Tuning CEF Load Balancing
In environments with a low number of IP hosts you have to fine-tune the CEF load-sharing algorithm to ensure that the traffic is spread between all parallel paths. A typical scenario is a primary-backup data center setup with pairs of replicating servers, as shown in the figure below.
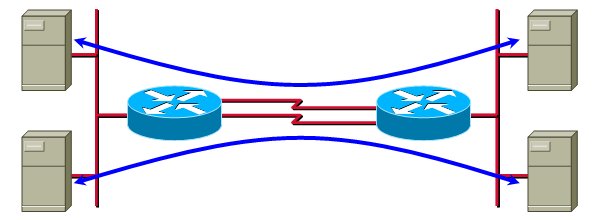
In these cases, you have to try different values of seed parameter of the CEF universal algorithm.
Local username authentication
Cisco IOS violates RFC 2616 (HTTP/1.1)
Update 2012-08-27: Stefan de Kooter reported the bug had been fixed in IOS release 15.1(4)M.
I simply had to check with the RFC; by setting the Host: field of HTTP request to an IP address (instead of a host name), Cisco IOS violates section 14.23 of RFC 2616, which says:
The Host request-header field specifies the Internet host and port number of the resource being requested, as obtained from the original URI given by the user or referring resource ... The Host field value MUST represent the naming authority of the origin server or gateway given by the original URL.
IOS HTTP client sets Host: field to IP address
Update 2012-08-27: Stefan de Kooter reported the bug had been fixed in IOS release 15.1(4)M.
If you run multiple web sites on a single physical server, it's highly likely that you rely on the ability of HTTP/1.1 clients to specify the Host: field in the HTTP request to indicate which web site they're trying to access.
Cisco IOS always inserts the web server's IP address (not the hostname) in the Host: field of the HTTP request, regardless of whether you enter IP address or hostname in the URL part of an IOS command that supports HTTP (for example, copy or more command) ... and regardless of whether the hostname is locally configured with the ip host command or resolved by an external DNS server specified in the ip name-server command.
End result: Cisco IOS-based routers (tested up to release 12.4(11)T) can access only the default web site on a web server hosting multiple web sites.
Log terminal access to your router
The configuration commands to enable terminal access logging are login on-success log and login on-failure log. You can also specify that you want send SNMP traps in these circumstances (with the trap option) or that you only want to log every Nth attempt with the every n option.
